This was brought to my attention a few days ago over email. Say one hosts on an internal web server a wiki/documentation web site or so for internal use.
Various content is created on that wiki. And there is a possibility to have linked external web pages for references, directions etc. on this internal web site.
Depending what we use on this web server for the wiki/documentation web site or if this web site does not use SSL, the Referer HTTP header may introduce some privacy issues, revealing internal URLs.
http://en.wikipedia.org/wiki/HTTP_referer
For example, here is a Wireshark capture taken on a client behind a Forefront TMG Beta 3 firewall(yeah I know is not ISA Server 2006 firewall), the client is viewing a web page located on an internal web server(using HTTP) and on this web page there is an external link. When it clicks on that link we can spot bellow the GET request made for the external web page, and the Referer HTTP header which contains the internal URL:
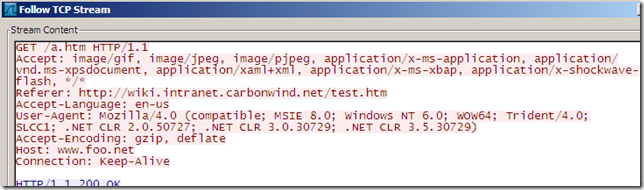
And here is the GET request reaching the external web server(note the Via header introduced by Forefront TMG Beta 3):
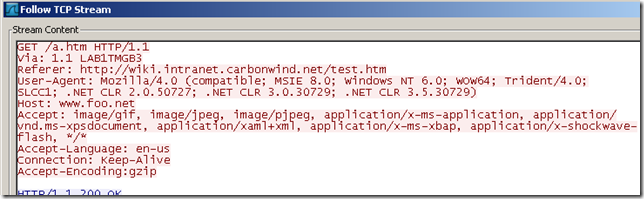
If we use SSL on our intranet web server on all web pages, and have the above linked external address on a web page, according to RFC 2616 the browser should not sent the Referer HTTP header as the referring web page was viewed under SSL and we make a HTTP request for the linked external URL:
http://www.w3.org/Protocols/rfc2616/rfc2616-sec15.html
Clients SHOULD NOT include a Referer header field in a (non-secure) HTTP request if the referring page was transferred with a secure protocol.
The HTTP filter on ISA Server 2006 is not very powerful when it comes to modifying the HTTP headers in requests or responses. We can have the Via header modified so to prevent the leak of ISA’s name to address other privacy issue, but we cannot have that header stripped.
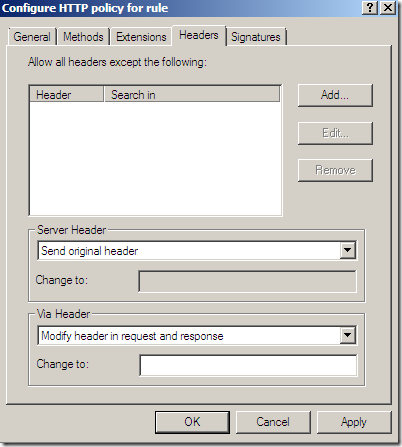
Now, we may be able to control the sending of the Referer HTTP header at the browser level or on our wiki/documentation web site itself, but one may want to do that on the proxy level too as an extra precaution method.
And we may have the following: say we may want to strip/modify the Referer HTTP header only when it contains intranet links, otherwise to pass the Referer HTTP header unmodified.
Unfortunately I don’t think this is possible by default on ISA Server from the mmc. However there might be an ISA add-on that may help you if want to strip/modify the Referer HTTP header with ISA Server 2006, IsaScript from Collective Software. I haven’t tried, but at a glance it seems feasible to strip/modify the Referer HTTP header on ISA Server 2006 with IsaScript.