As you are aware Microsoft released yesterday a security update, KB974571, which fixes certain Windows CryptoAPI vulnerabilities made public a while ago(from the press). For more details about what this security update fixes please refer to:
http://www.microsoft.com/technet/security/bulletin/ms09-056.mspx
Since ISA Server 2004/2006 & Forefront TMG RC make use of the Windows CryptoAPI in certain operations, this vulnerability can affect certain ISA Server 2004/2006 & Forefront TMG RC deployments, like:
[1] - on ISA Server 2004/2006 & Forefront TMG RC: the reverse proxy scenario when SSL bridging (HTTPS-to-HTTPS bridging) is used.
[2] - on Forefront TMG RC: the Outbound HTTPS Inspection.
[3] - the privacy offered by SSL to the Forefront TMG RC URL Filtering using Microsoft Reputation Service Beta.
[1] For example, the scenario when ISA Server 2004/2006 & Forefront TMG RC act as a reverse proxy and publish a secure web server using what is known as SSL bridging (HTTPS-to-HTTPS bridging) in order to decrypt the traffic protected by SSL and apply application layer inspection.
http://technet.microsoft.com/en-us/library/cc995200.aspx
In this case, ISA Server 2004/2006 & Forefront TMG RC do a check over the server’s name(CN or SAN) from the server certificate(inspects the server’s certificate) used on the backend published server. An internal attacker(depending on the network layout) might be able to defeat the protection offered by the SSL bridging (HTTPS-to-HTTPS bridging) using an active MITM attack and a crafted certificate(Null character within CN, see the bellow example when I’ve opened such a certificate within ASN.1 Editor, if the certificate was not revoked or ISA is unaware by this fact) and intercept the traffic between ISA and the backend published secure web site.
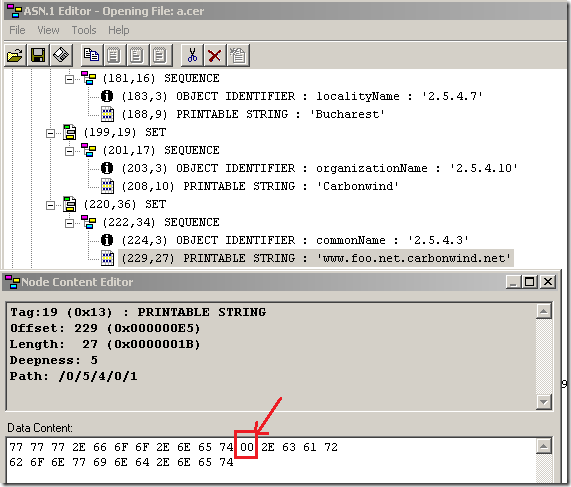
To picture this aspect for ISA Server 2006:
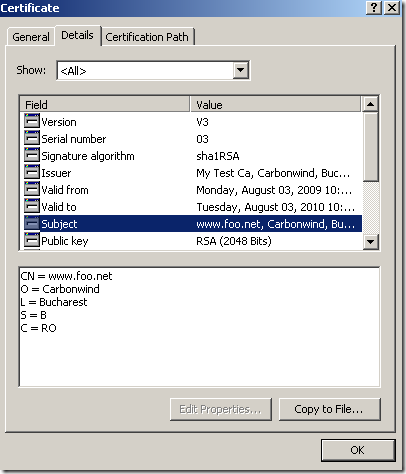
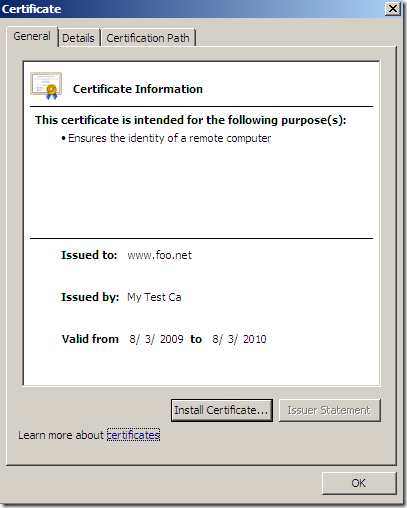
a) - ISA Server on unpatched Windows Server 2003 R2 SE SP2, reverse proxy scenario when SSL bridging (HTTPS-to-HTTPS bridging) is used, active MITM, the certificate the attacker presents to ISA in reality was not issued to www.foo.net(but on unpatched Windows Server 2003 R2 SE SP2 can’t tell the difference):
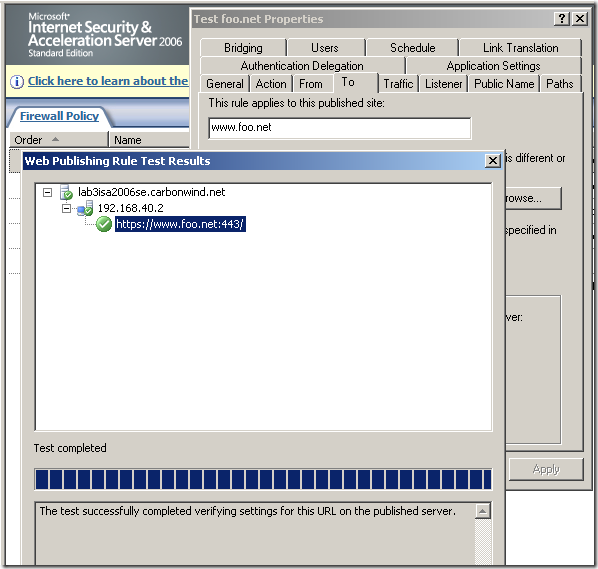
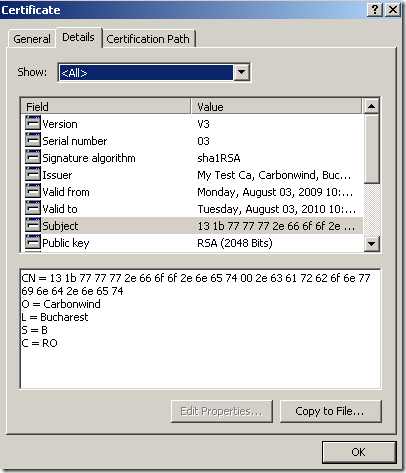
b) - ISA Server on patched Windows Server 2003 R2 SE SP2, reverse proxy scenario when SSL bridging (HTTPS-to-HTTPS bridging) is used, active MITM, the certificate the attacker presents to ISA in reality was not issued to www.foo.net:
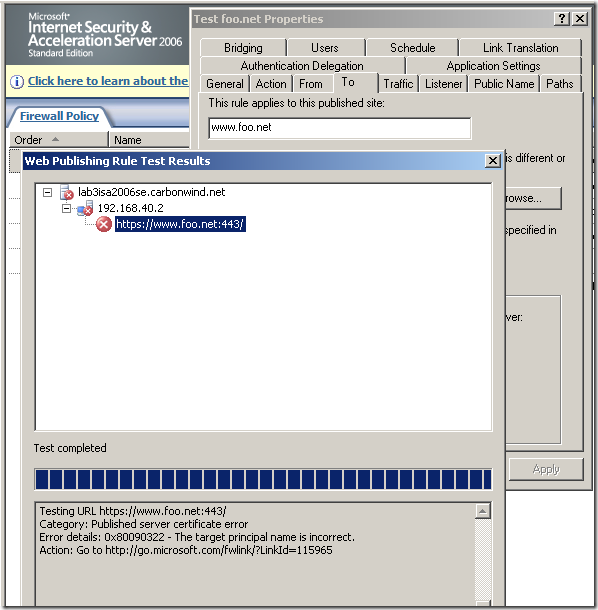
Same example for Forefront TMG RC:
a) Forefront TMG RC on unpatched Windows Server 2008 R2 SE, reverse proxy scenario when SSL bridging (HTTPS-to-HTTPS bridging) is used, active MITM, the certificate the attacker presents to TMG in reality was not issued to www.foo.net(but on unpatched Windows Server 2008 R2 can’t tell the difference):
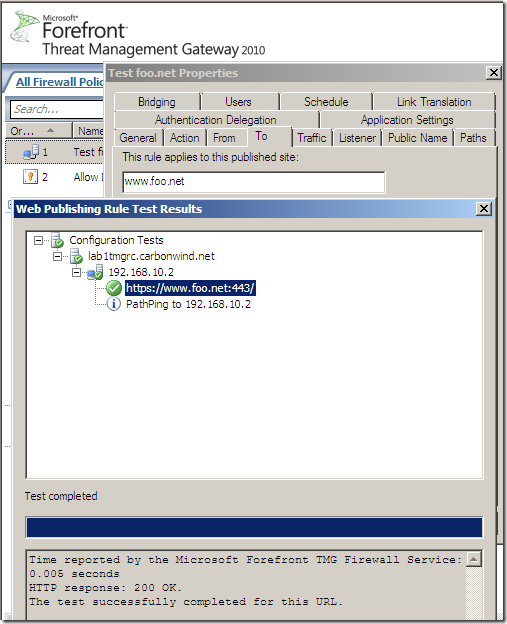
b) Forefront TMG RC on patched Windows Server 2008 R2 SE, reverse proxy scenario when SSL bridging (HTTPS-to-HTTPS bridging) is used, active MITM, the certificate the attacker presents to TMG in reality was not issued to www.foo.net:
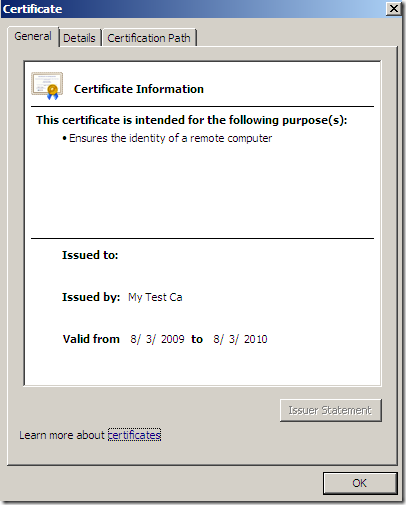
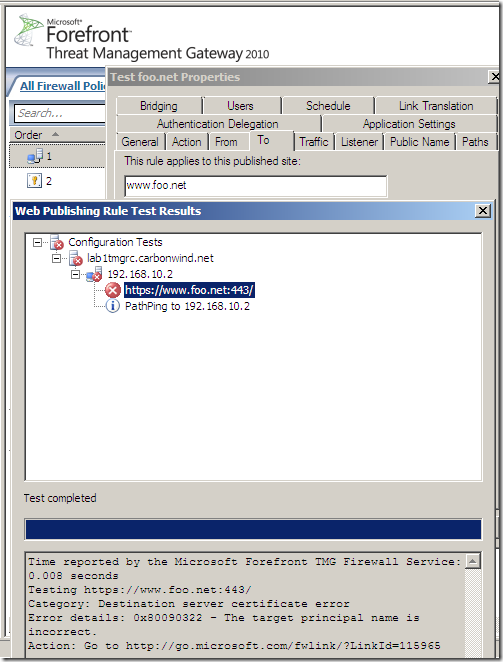
[2]Also, for Forefront TMG RC the Outbound HTTPS Inspection might be susceptible to a CN Null character certificate attack as an attacker might successfully spoof the digital certificate of an external web site, and while the Outbound HTTPS Inspection does inspect the server’s certificate(verify the server’s name from the server certificate and check the status of the certificate), due to the CN Null character certificate attack, it may fail to “read” the correct name from that certificate(in case this certificate was not revoked or TMG is unaware by this fact).
We’ve discussed this aspect here.
An example:
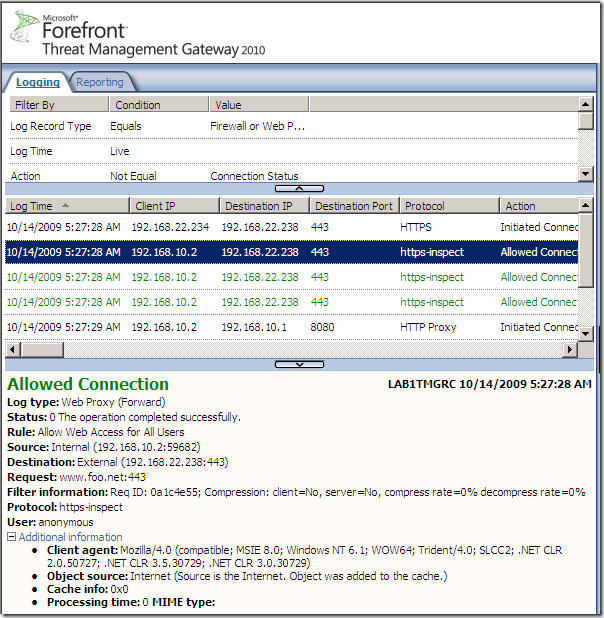
a) Forefront TMG RC on unpatched Windows Server 2008 R2 SE, Outbound HTTPS Inspection scenario, active MITM, the certificate the attacker presents to TMG in reality was not issued to www.foo.net(but on unpatched Windows Server 2008 R2 can’t tell the difference):
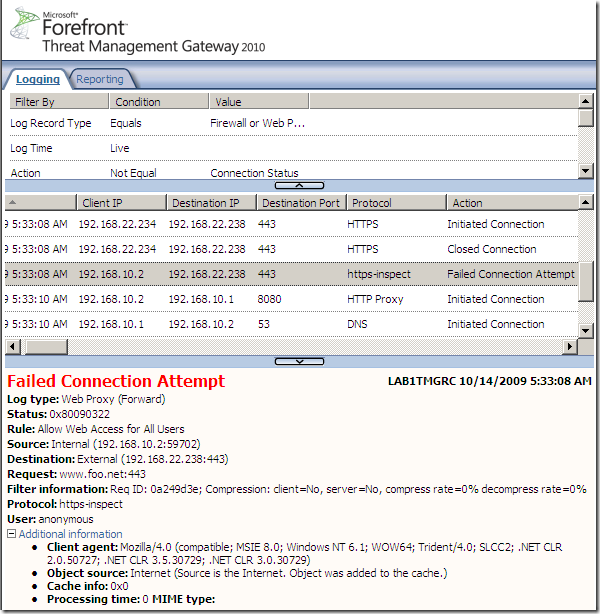
b) Forefront TMG RC on patched Windows Server 2008 R2 SE, Outbound HTTPS Inspection scenario, active MITM, the certificate the attacker presents to TMG in reality was not issued to www.foo.net(note the error code from bellow):
[3] The privacy offered by SSL to the Forefront TMG RC URL Filtering using Microsoft Reputation Service Beta.
We’ve described a little this service here(note that the FQDN mention there might have changed as writing).
The potential impact of this aspect may be lower compared to the above mentioned two scenarios.
Above we’ve taken a quick look at some possible scenarios when the MS09-056 security bulletin(rated as Important) may impact ISA Server 2004/2006 & Forefront TMG RC operations.
As usual, make sure your machines are up-to-date(as this time Windows vulnerabilities may affect ISA Server 2004/2006 & Forefront TMG RC operations).