According to this, in respect with the excluding destinations from Outbound HTTPS inspection on Forefront TMG 2010:
By default, Forefront TMG inspects the validity of the HTTPS certificate for each of the Web sites excluded from HTTPS inspection, thereby providing some minimal security. If you do not want Forefront TMG to perform this security check for a given site, click the site, and then click No Validation.

In the same document, for the excluding sources from HTTPS inspection, there is no mention about a certificate validation:
So, let’s test:
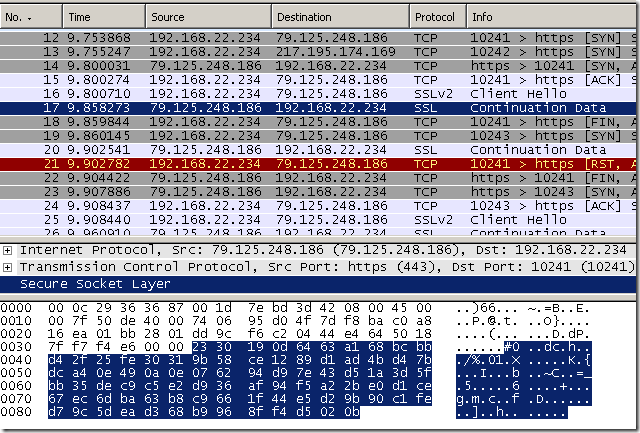
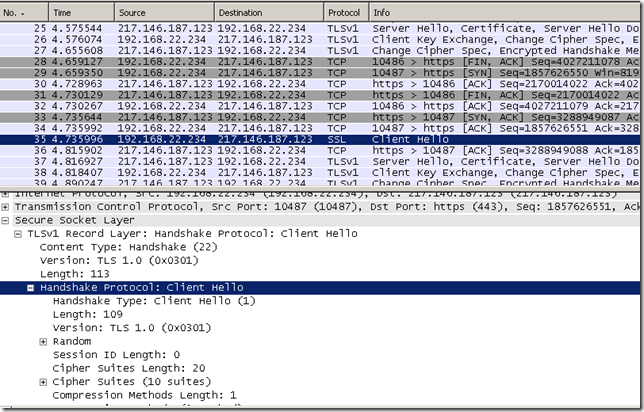
- web proxy client, source client excluded from the HTTPS inspection, we’ve got a certificate check, note the protocol from TMG’s logs:
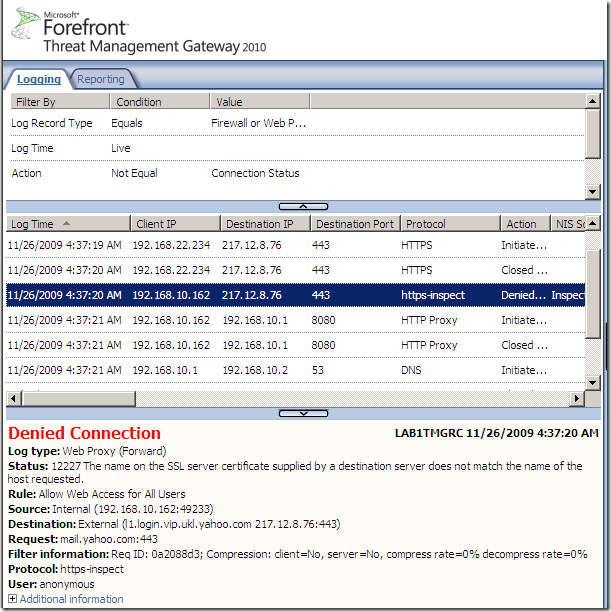
- SecureNAT client, source client excluded from the HTTPS inspection, apparently we don’t have a check on the server’s certificate, but Forefront TMG 2010 still connects to the server(maybe to check if it can use SSL/TLS ? just guessing…):
How can we notice this ?
By looking at the Client Hello messages, I don’t use SSL 2.0 on the client and I have only 10 cipher suites enabled on it, so first is the Client Hello message used by the HTTPS Inspection on Forefront TMG, then is my client’s Hello message, note the protocol from TMG’s logs:
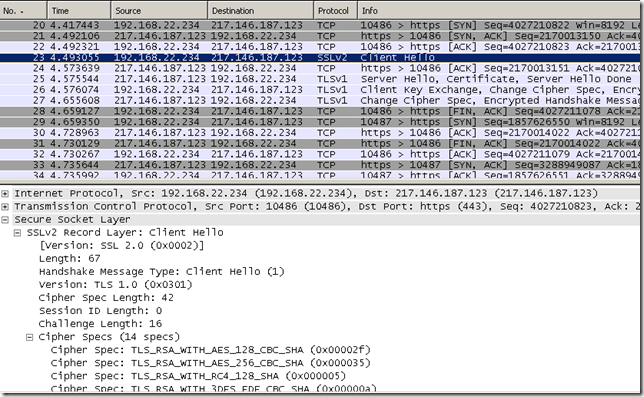
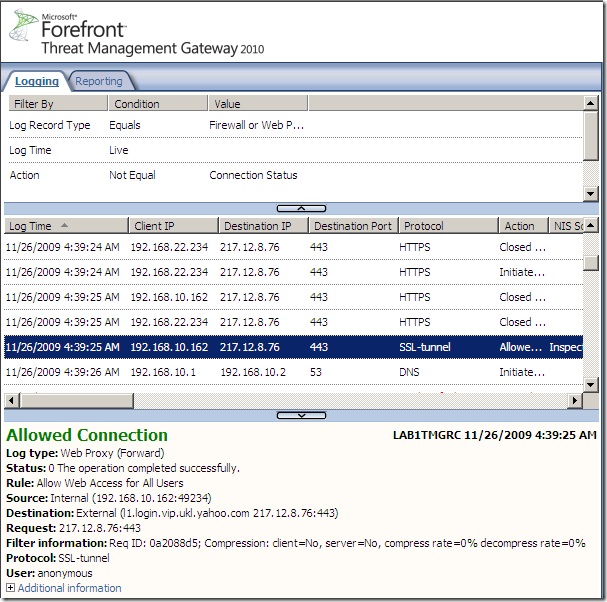
Actually it still connects “before” when excluding destinations and configure them for no validation.
This can be great from a security point of view if it tries to see if the server can speak SSL/TLS.
But this “behavior” might lead us to a jam sometimes.
For example today I thought to try to use Skype behind Forefront TMG 2010. Knowing that Skype does not really use SSL/TLS, I’ve decided to add my machine(SecureNAT client) to the Source Exceptions tab of the HTTPS Inspection as I can’t exclude destinations due to Skype’s p2p nature(even if I could I don’t think it would matter due to the connect “before” behavior).
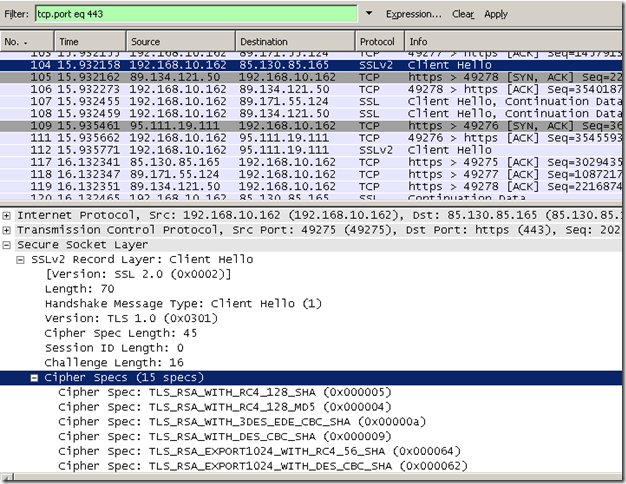
Skype is quite sneaky, it tried as SecureNAT and also it detected the proxy and attempted to use(CONNECT method) the proxy for TCP port 443(the rest of the ports were blocked and it could not go out on TCP port 80).
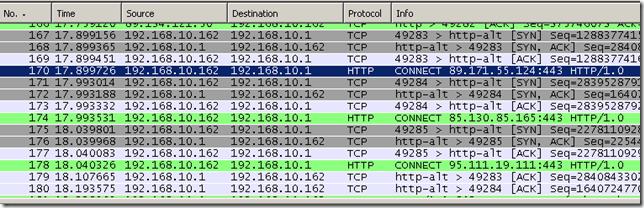
Which on Forefront TMG 2010 translated into:
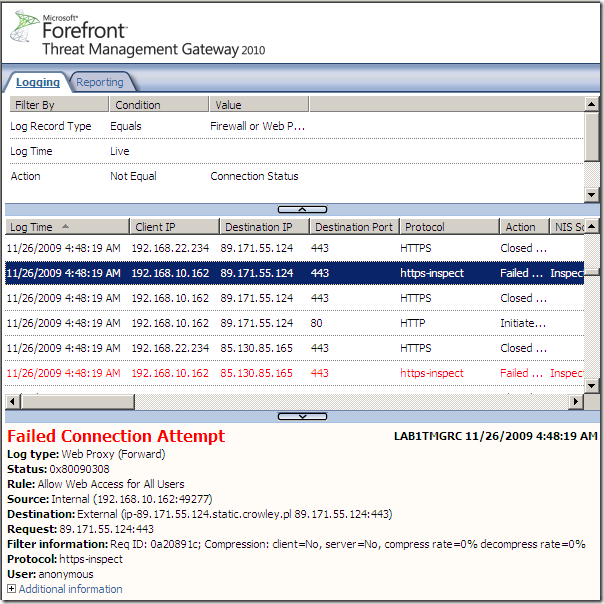
The error code seem to indicate a SSL/TLS error(which at a glance seem illogical since we have a source exclusion for our client).
Actually if we take a Wireshark trace on Forefront TMG 2010’s external interface, apparently it(Forefront TMG 2010) tries to connect to the specified destination in order to obtain its certificate to verify it, which cannot do as Skype does not use true SSL/TLS, which leads to the termination of the client’s attempts(either as SecureNAT or web proxy client):