I’ve got this question on email(probably meaning scan what’s inside an .xpi file).
So does it scan ?
I don't know, let’s see.
The .xpi files essentially are ZIP files.
Since the Malware Inspection is able to scan (inside) ZIP files, it might be able to scan (inside) .xpi files too.
I’ve “made” my own extension file(actually I’ve downloaded one from Mozilla’s add-ons web site and “bundle” it with the Eicar test virus) and put in on a local web server on my lab.
If I try to access with Firefox behind a TMG machine(the default settings for the Malware Inspection are in place) the “malware” extension, this happens:
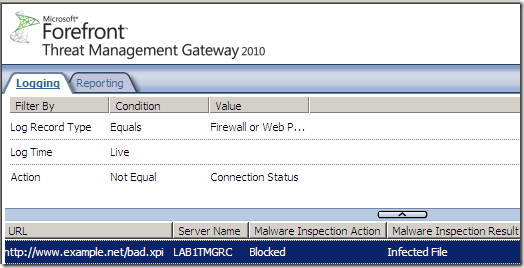
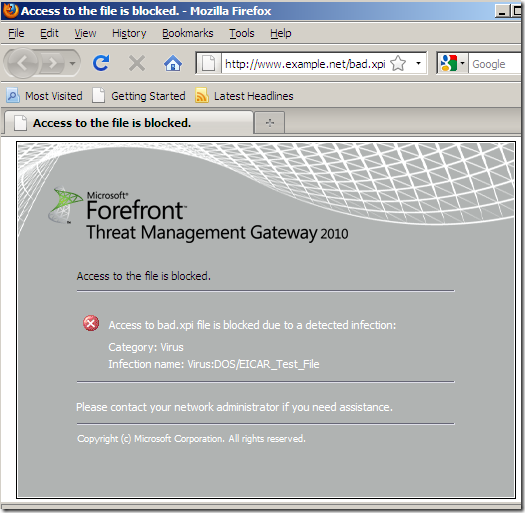
So it looks like it does scan (inside) such files. If it will detect anything, this would be up to the inspection engines.
If the add-ons are downloaded over HTTPS, this isn't a problem either, as Forefront TMG 2010 RTM is able to perform Outbound HTTPS Inspection and apply the Malware Inspection to HTTPS traffic:
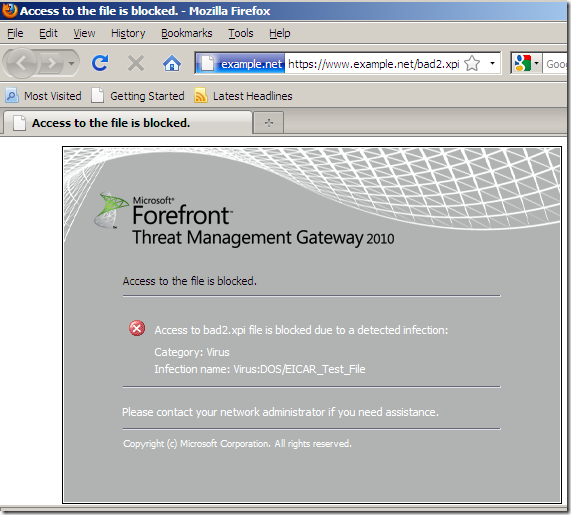
Note that Extended Validation (EV) SSL is not supported with HTTPS inspection(the EV visibility that is offered by some web browsers, will not be displayed in users’ browsers). addons.mozilla.org uses an EV certificate, so expect not to see the green bar on Firefox browsers behind TMG doing Outbound HTTPS Inspection.
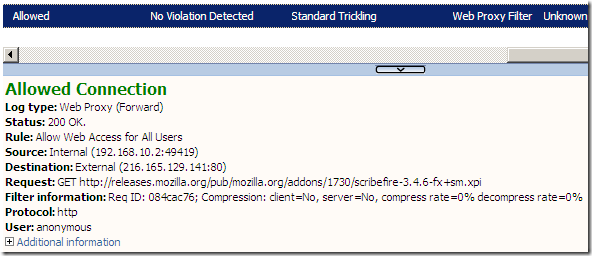
Anyway, apparently, the extension itself is downloaded over HTTP…
References:
- https://developer.mozilla.org/en/XPInstall
- https://developer.mozilla.org/en/Extension_Packaging
- http://en.wikipedia.org/wiki/XPInstall
- http://technet.microsoft.com/en-us/library/ee869540.aspx
- http://technet.microsoft.com/en-us/library/ee658156.aspx
- http://www.informationweek.com/news/internet/browsers/showArticle.jhtml?articleID=217700105