|
24.04.2008
Vyatta VC4 - Advanced VPN Site-to-Site Connections - Part 12 - Configure IPIP/IPsec in Case of Scenario 2 Using IPsec ESP in Tunnel Mode and as IPIP Tunnel Endpoints Private IP Addresses from the Loopback Interfaces
- 1. Vyatta HQ IPIP/IPsec Config
- 2. Vyatta Branch1 IPIP/IPsec Config
- 3. Vyatta Branch2 IPIP/IPsec Config
- 4. Make The hub-and-spoke Topology a Mesh One
In Part 11 we've configured GRE/IPsec, now let's configure IPIP/IPsec in case of Scenario 2. If you do not recall what was Scenario 2 take a look here.
As in Part 11, due to the reasons mentioned there, we will use for the IPIP tunnel endpoints private IP addresses from the loopback interfaces and IPsec ESP in tunnel mode.
So we are going to use the working configuration (adjusting it for IPIP tunnels) suggested by Stig for GRE/IPsec on vyatta.org/forum. You may like to read the entire thread.
As before, I will enable VMware Network Adapter VMnet5, VMware Network Adapter VMnet6, VMware Network Adapter VMnet7 on the host machine, see Figure180.
Figure180: VMware Network Adapters VMnet5, VMnet6 and VMnet7 Enabled
Also, since VMware Network Adapters VMnet5, VMnet6 and VMnet7 are enabled, I can use a SSH client from the host machine to configure the routers.
And before entering the configuration lines on the Vyatta VC4 machines, I will start a Wireshark capture on the VMnet5 interface on the host machine(see Figure181, make sure "Capture packets in promiscous mode " is selected). Doing so, I will have a nice point of view over the traffic sent between Vyatta VC4 machines because Vyatta HQ represents the hub, I will see the first packets sent through the tunnels, the OSPF multicast packets and so on. This is very useful for troubleshooting and we can actually see how things work. Additionally you can start Wireshark captures on VMnet6 and VMnet7 interfaces on the host machine in order to have a complete view over the traffic(see Figure182 and Figure183, make sure "Capture packets in promiscous mode " is selected).
Figure181: Start a Wireshark capture on the VMnet5 interface on the host machine
Figure182: Wireshark Capture Menu: Interfaces
Figure183: Start the Wireshark captures on the host machine
1. Vyatta HQ IPIP/IPsec Config
On the Vyatta HQ machine, since we are using a hub-and-spoke topology and Vyatta HQ is the hub, we will create two IPIP tunnels, one to Branch1 and the other to Branch2. Also we will create two IPsec VPN site-to-site connections, one to Branch1(to protect the IPIP tunnel between HQ and Branch1), and the other to Branch2(to protect the IPIP tunnel between HQ and Branch2).
Configure the loopback interface with two IP addresses which will serve as local IPIP tunnel endpoints(one for the IPIP tunnel between HQ and Branch1 and the other for the IPIP tunnel between HQ and Branch2). And commit your settings.
set interfaces loopback lo address 192.168.200.1/24
set interfaces loopback lo address 192.168.210.1/24
commit
Configure two IPIP tunnels. The remote-ip (remote tunnel endpoint) will be the IP address configured on the loopback interface of Vyatta Branch1 for the IPIP tunnel between HQ and Branch1, and respectively the IP address configured on the loopback interface of Vyatta Branch2 for the IPIP tunnel between HQ and Branch2.
I will not commit my settings yet, because I want to protect the tunnels first, so that no packet can travel in clear.
set interfaces tunnel tun1
set interfaces tunnel tun1 address 192.168.111.1/30
set interfaces tunnel tun1 description "IPIP Tunnel to Branch1"
set interfaces tunnel tun1 encapsulation ipip
set interfaces tunnel tun1 local-ip 192.168.200.1
set interfaces tunnel tun1 remote-ip 192.168.220.1
set interfaces tunnel tun2
set interfaces tunnel tun2 address 192.168.121.1/30
set interfaces tunnel tun2 description "IPIP Tunnel to Branch2"
set interfaces tunnel tun2 encapsulation ipip
set interfaces tunnel tun2 local-ip 192.168.210.1
set interfaces tunnel tun2 remote-ip 192.168.230.1
And the VPN configuration. I've configured an ike-group and an esp-group (by default IPsec ESP in tunnel mode is used).
And two IPsec VPN site-to-site connections, one to Branch1(to protect the IPIP tunnel between HQ and Branch1), and the other to Branch2(to protect the IPIP tunnel between HQ and Branch2). Note the local and remote subnets in both cases.
Since this is a simple test, I will use pre-shared keys for authentication.
I will commit my configuration.
set vpn ipsec ipsec-interfaces interface eth0
set vpn ipsec ike-group IKE-IPIP proposal 1
set vpn ipsec ike-group IKE-IPIP proposal 1 encryption aes128
set vpn ipsec ike-group IKE-IPIP proposal 1 hash sha1
set vpn ipsec ike-group IKE-IPIP proposal 1 dh-group 5
set vpn ipsec ike-group IKE-IPIP lifetime 28800
set vpn ipsec esp-group ESP-IPIP proposal 1
set vpn ipsec esp-group ESP-IPIP proposal 1 encryption aes128
set vpn ipsec esp-group ESP-IPIP proposal 1 hash sha1
set vpn ipsec esp-group ESP-IPIP pfs
set vpn ipsec esp-group ESP-IPIP lifetime 3600
set vpn ipsec site-to-site peer 192.168.60.2 authentication mode pre-shared-secret
edit vpn ipsec site-to-site peer 192.168.60.2
set authentication pre-shared-secret 12345
set ike-group IKE-IPIP
set local-ip 192.168.50.2
set tunnel 1 local-subnet 192.168.200.1/32
set tunnel 1 remote-subnet 192.168.220.1/32
set tunnel 1 esp-group ESP-IPIP
top
set vpn ipsec site-to-site peer 192.168.70.2 authentication mode pre-shared-secret
edit vpn ipsec site-to-site peer 192.168.70.2
set authentication pre-shared-secret 67890
set ike-group IKE-IPIP
set local-ip 192.168.50.2
set tunnel 1 local-subnet 192.168.210.1/32
set tunnel 1 remote-subnet 192.168.230.1/32
set tunnel 1 esp-group ESP-IPIP
top
commit
And we will run OSPF through these tunnels to discover the networks behind the other Vyatta VC4 machines.
set protocols ospf area 100
set protocols ospf area 100 network 192.168.10.0/24
set protocols ospf area 100 network 192.168.111.0/30
set protocols ospf area 100 network 192.168.121.0/30
set protocols ospf log-adjacency-changes
commit
save
2. Vyatta Branch1 IPIP/IPsec Config
On the Vyatta Branch1 machine, which will be a spoke, we will create one IPIP tunnel, to Vyatta HQ. And one IPsec VPN site-to-site connection, to Vyatta HQ(to protect the IPIP tunnel between Branch1 and HQ).
Configure the loopback interface with one IP address which will serve as the local IPIP tunnel endpoint(for the IPIP tunnel between Vyatta Branch1 and Vyatta HQ). And commit your settings.
set interfaces loopback lo address 192.168.220.1/24
commit
Configure the IPIP tunnel. The remote-ip (remote tunnel endpoint) will be the first IP address configured on the loopback interface of Vyatta HQ.
As before, I will not commit my settings yet, because I want to protect the tunnel first, so that no packet can travel in clear.
set interfaces tunnel tun1
set interfaces tunnel tun1 address 192.168.111.2/30
set interfaces tunnel tun1 description "IPIP Tunnel to HQ"
set interfaces tunnel tun1 encapsulation ipip
set interfaces tunnel tun1 local-ip 192.168.220.1
set interfaces tunnel tun1 remote-ip 192.168.200.1
And the VPN configuration. I've configured an ike-group and an esp-group.
And one IPsec VPN site-to-site connection, to HQ(to protect the IPIP tunnel between HQ and Branch1). Note the local and remote subnets.
I will commit my configuration.
set vpn ipsec ipsec-interfaces interface eth0
set vpn ipsec ike-group IKE-IPIP proposal 1
set vpn ipsec ike-group IKE-IPIP proposal 1 encryption aes128
set vpn ipsec ike-group IKE-IPIP proposal 1 hash sha1
set vpn ipsec ike-group IKE-IPIP proposal 1 dh-group 5
set vpn ipsec ike-group IKE-IPIP lifetime 28800
set vpn ipsec esp-group ESP-IPIP proposal 1
set vpn ipsec esp-group ESP-IPIP proposal 1 encryption aes128
set vpn ipsec esp-group ESP-IPIP proposal 1 hash sha1
set vpn ipsec esp-group ESP-IPIP pfs
set vpn ipsec esp-group ESP-IPIP lifetime 3600
set vpn ipsec site-to-site peer 192.168.50.2 authentication mode pre-shared-secret
edit vpn ipsec site-to-site peer 192.168.50.2
set authentication pre-shared-secret 12345
set ike-group IKE-IPIP
set local-ip 192.168.60.2
set tunnel 1 local-subnet 192.168.220.1/32
set tunnel 1 remote-subnet 192.168.200.1/32
set tunnel 1 esp-group ESP-IPIP
top
commit
And we will run OSPF through this tunnel to discover the networks behind the other Vyatta VC4 machines.
set protocols ospf area 100
set protocols ospf area 100 network 192.168.30.0/24
set protocols ospf area 100 network 192.168.111.0/30
set protocols ospf log-adjacency-changes
commit
save
3. Vyatta Branch2 IPIP/IPsec Config
On the Vyatta Branch2 machine, which will be a spoke, we will create one IPIP tunnel, to Vyatta HQ. And one IPsec VPN site-to-site connection, to Vyatta HQ(to protect the IPIP tunnel between Branch2 and HQ).
Configure the loopback interface with one IP address which will serve as the local IPIP tunnel endpoint(for the IPIP tunnel between Vyatta Branch2 and Vyatta HQ). And commit your settings.
set interfaces loopback lo address 192.168.230.1/24
commit
Configure the IPIP tunnel. The remote-ip (remote tunnel endpoint) will be the second IP address configured on the loopback interface of Vyatta HQ.
As before, I will not commit my settings yet, because I want to protect the tunnel first, so that no packet can travel in clear.
set interfaces tunnel tun1
set interfaces tunnel tun1 address 192.168.121.2/30
set interfaces tunnel tun1 description "IPIP Tunnel to HQ"
set interfaces tunnel tun1 encapsulation ipip
set interfaces tunnel tun1 local-ip 192.168.230.1
set interfaces tunnel tun1 remote-ip 192.168.210.1
And the VPN configuration. I've configured an ike-group and an esp-group.
And one IPsec VPN site-to-site connection, to HQ(to protect the IPIP tunnel between HQ and Branch2). Note the local and remote subnets.
I will commit my configuration.
set vpn ipsec ipsec-interfaces interface eth0
set vpn ipsec ike-group IKE-IPIP proposal 1
set vpn ipsec ike-group IKE-IPIP proposal 1 encryption aes128
set vpn ipsec ike-group IKE-IPIP proposal 1 hash sha1
set vpn ipsec ike-group IKE-IPIP proposal 1 dh-group 5
set vpn ipsec ike-group IKE-IPIP lifetime 28800
set vpn ipsec esp-group ESP-IPIP proposal 1
set vpn ipsec esp-group ESP-IPIP proposal 1 encryption aes128
set vpn ipsec esp-group ESP-IPIP proposal 1 hash sha1
set vpn ipsec esp-group ESP-IPIP pfs
set vpn ipsec esp-group ESP-IPIP lifetime 3600
set vpn ipsec site-to-site peer 192.168.50.2 authentication mode pre-shared-secret
edit vpn ipsec site-to-site peer 192.168.50.2
set authentication pre-shared-secret 67890
set ike-group IKE-IPIP
set local-ip 192.168.70.2
set tunnel 1 local-subnet 192.168.230.1/32
set tunnel 1 remote-subnet 192.168.210.1/32
set tunnel 1 esp-group ESP-IPIP
top
commit
And we will run OSPF through this tunnel to discover the networks behind the other Vyatta VC4 machines.
set protocols ospf area 100
set protocols ospf area 100 network 192.168.40.0/24
set protocols ospf area 100 network 192.168.121.0/30
set protocols ospf log-adjacency-changes
commit
save
If we take a look at the Wireshark capture, we will notice that it recorded some activity, a sign that our "tunnels" are working. In Figure184 we can spot the IKE Phase II and II negotiations between HQ and Branch1, and between HQ and Branch2.
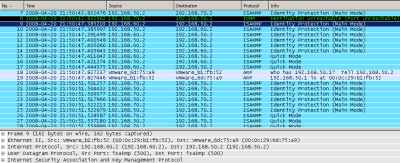
Figure184: Wireshark Capture IPIP/IPsec
Let's check the routing table on the Vyatta HQ, Vyatta Branch1 and Vyatta Branch2, see Figure185, Figure186 and Figure187 . We can notice that every Vyatta VC4 machine is now aware of the networks behind the other Vyatta VC4 machines.
And spot the kernel routes we were talking about at the beginning at this part. If we were using IPsec ESP in transport mode with Vyatta VC4, we would not specify the "remote-subnet " and the "local-subnet". However, for example on Vyatta HQ, for the site-to-site VPN connection between Vyatta HQ and Vyatta Branch1, Openswan will add a kernel route that would say that 192.168.60.2/32 is directly connected, eth0. Obviously this is not true. To make the VPN tunnel work we would need to manually delete the kernel route. This would be also true for IPsec ESP in tunnel mode if for example on Vyatta HQ we would enter in the VPN configuration as "remote-subnet" 192.168.60.2/32 (the remote IPIP tunnel endpoint as in Part 10) instead of 192.168.220.0/24, and as "local-subnet" 192.168.50.2/32 (the local IPIP tunnel endpoint as in Part 10) instead of 192.168.200.0/24. Again the kernel route would say that 192.168.60.2/32 is directly connected, eth0. So to make the VPN tunnel work we would need to manually delete the kernel route.
With the IPIP tunnel endpoints private IP addresses from loopback interfaces, we are not particularly concerned about the kernel routes.
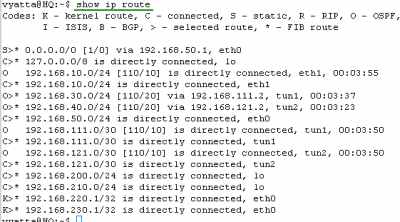
Figure185: Vyatta HQ IPIP/IPsec: Routing Table
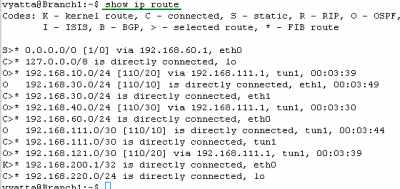
Figure186: Vyatta Branch1 IPIP/IPsec: Routing Table
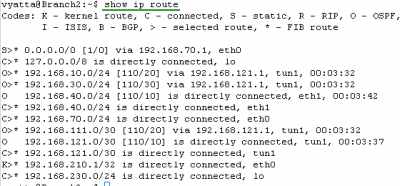
Figure187: Vyatta Branch2 IPIP/IPsec: Routing Table
Let's look at the OSPF information about the tunnel interfaces on the Vyatta HQ, Vyatta Branch1 and Vyatta Branch2 (note the MTU too, the default one, you can modify it if necessary), see Figure188, Figure189 and Figure190.
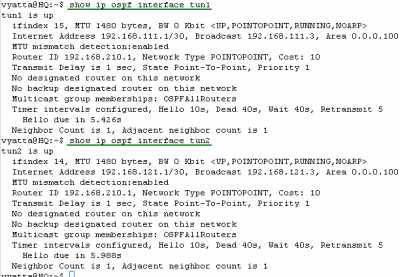
Figure188: Vyatta HQ IPIP/IPsec: show ip ospf interface tun1 and tun2
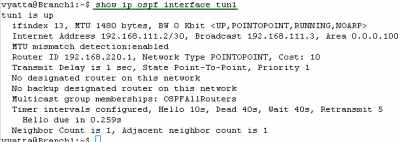
Figure189: Vyatta Branch1 IPIP/IPsec: show ip ospf interface tun1
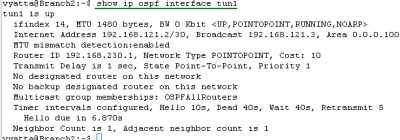
Figure190: Vyatta Branch2 IPIP/IPsec: show ip ospf interface tun1
Let's look at some VPN information (IKE and IPsec SAs) on the Vyatta HQ, Vyatta Branch1 and Vyatta Branch2, see Figure191, Figure192 and Figure193.
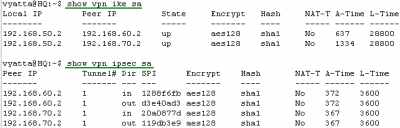
Figure191: Vyatta HQ IPIP/IPsec: VPN Info
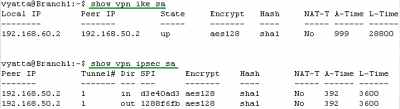
Figure192: Vyatta Branch1 IPIP/IPsec: VPN Info
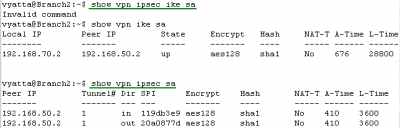
Figure193: Vyatta Branch2 IPIP/IPsec: VPN Info
Let's see if we have connectivity between hosts located behind Vyatta VC4 machines, see Figure194, Figure195 and Figure196.
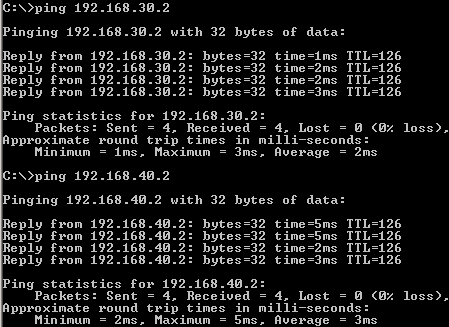
Figure194: IPIP/IPsec: Ping from a Host Behind Vyatta HQ to Hosts Behind Vyatta Branch1 and Vyatta Branch2
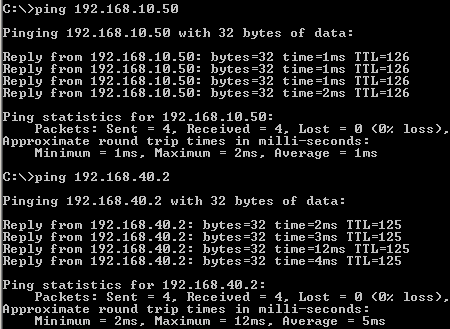
Figure195: IPIP/IPsec: Ping from a Host Behind Vyatta Branch1 to Hosts Behind Vyatta HQ and Vyatta Branch2
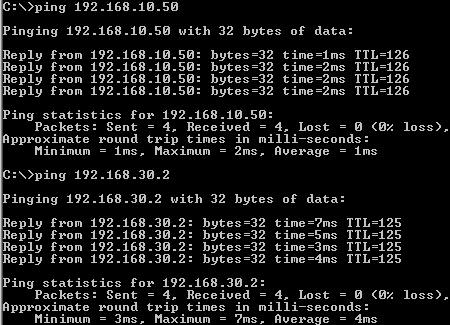
Figure196: IPIP/IPsec: Ping from a Host Behind Vyatta Branch2 to Hosts Behind Vyatta HQ and Vyatta Branch1
Things look good.
All the configuration lines entered on Vyatta HQ, Vyatta Branch1 and Vyatta Branch2 can be found here:
- Vyatta HQ
- Vyatta Branch1
- Vyatta Branch2
4. Make The hub-and-spoke Topology a Mesh One
If you want, you can make the hub-and-spoke topology a mesh one, by configuring a IPIP tunnel between Branch1 and Branch2, and an IPsec VPN site-to-site connection between them to protect this IPIP tunnel.
On Branch1 add:
set interfaces loopback lo address 192.168.240.1/24
commit
set interfaces tunnel tun2
set interfaces tunnel tun2 address 192.168.131.1/30
set interfaces tunnel tun2 description "IPIP Tunnel to Branch2"
set interfaces tunnel tun2 encapsulation ipip
set interfaces tunnel tun2 local-ip 192.168.240.1
set interfaces tunnel tun2 remote-ip 192.168.250.1
set vpn ipsec site-to-site peer 192.168.70.2 authentication mode pre-shared-secret
edit vpn ipsec site-to-site peer 192.168.70.2
set authentication pre-shared-secret abcde
set ike-group IKE-IPIP
set local-ip 192.168.60.2
set tunnel 1 local-subnet 192.168.240.1/32
set tunnel 1 remote-subnet 192.168.250.1/32
set tunnel 1 esp-group ESP-IPIP
top
commit
set protocols ospf area 100 network 192.168.131.0/30
commit
On Branch2 add:
set interfaces loopback lo address 192.168.250.1/24
commit
set interfaces tunnel tun2
set interfaces tunnel tun2 address 192.168.131.2/30
set interfaces tunnel tun2 description "IPIP Tunnel to Branch1"
set interfaces tunnel tun2 encapsulation ipip
set interfaces tunnel tun2 local-ip 192.168.250.1
set interfaces tunnel tun2 remote-ip 192.168.240.1
set vpn ipsec site-to-site peer 192.168.60.2 authentication mode pre-shared-secret
edit vpn ipsec site-to-site peer 192.168.60.2
set authentication pre-shared-secret abcde
set ike-group IKE-IPIP
set local-ip 192.168.70.2
set tunnel 1 local-subnet 192.168.250.1/32
set tunnel 1 remote-subnet 192.168.240.1/32
set tunnel 1 esp-group ESP-IPIP
top
set protocols ospf area 100 network 192.168.131.0/30
commit
In Part 13 we will try to interoperate with a Cisco router when using GRE/IPsec with Vyatta VC4.
|