Say you’ve just deployed a lab for testing SSTP including:
- Windows 2008 R2 RC as the RRAS server and the NPS server
- Windows 2008 R2 RC as the DC and enterprise CA(Active Directory Certificate Services role-the certification authority (CA)- and Certification Authority Web Enrollment-the service that enables the issuing of certificates through a Web browser- were installed, IIS was also installed as a required role service for Certification Authority Web Enrollment)
- and Windows 7 RC as the SSTP VPN client.
For various reasons, you may want to be able to quickly establish a SSTP connection, for example my Windows 7 RC machine(the SSTP VPN client) is not a domain member, only the RRAS server is a domain member.
You’ve imported the CA’s certificate on the client, within the Certificates Computer Store, Trusted Root Certificates Authorities.
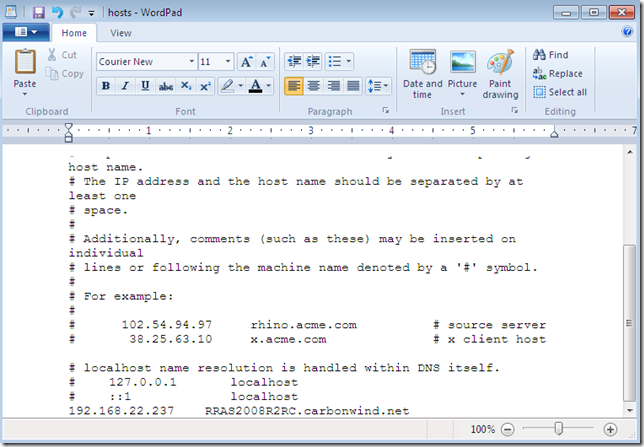
Quickly edited the hosts file on the client and added the hostname of the VPN server(the needed certificate was issued to the FQDN name of the VPN server-in my case I’ve issued a computer certificate to the VPN server using the mmc and the Computer Certificate template-, and so the client uses the FQDN name of the server in the VPN connection).
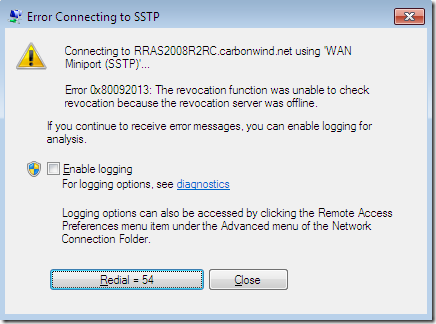
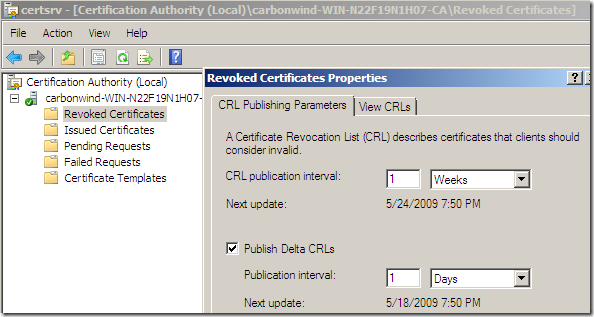
But the CRL check “stops” your SSTP connection because you’ve not published yet the HTTP CRL distribution point(in fact, within the bellow lines, I’ve not configured a “HTTP CRL distribution point”, just the ldap one is present within the server’s certificate) and the “stringent” CRL check was not disabled(disabling the CRL check may be acceptable in a lab), so the client cannot download the CRL:
VPN server’s certificate:
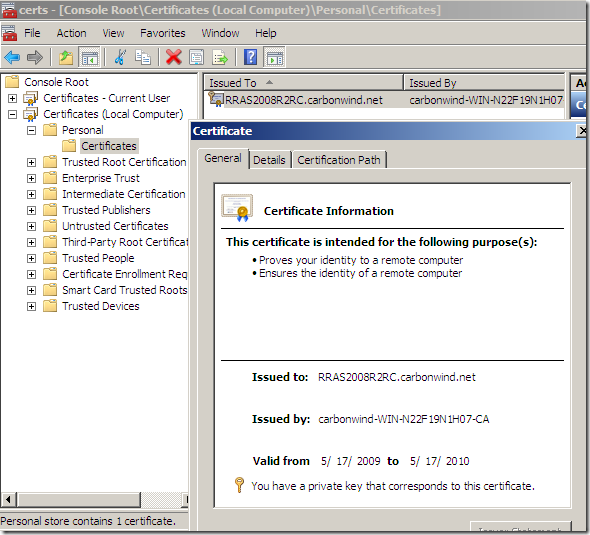
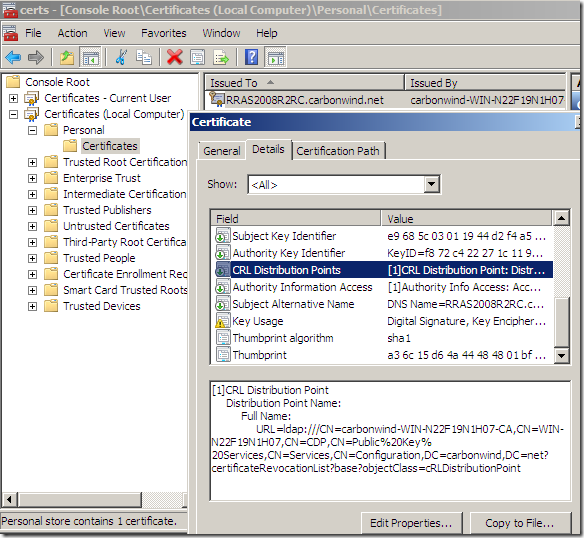
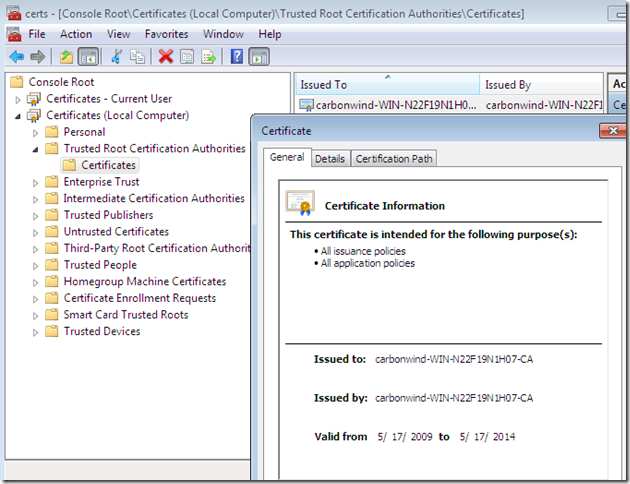
CA’s certificate imported on the client, within the Certificates Computer Store, Trusted Root Certificates Authorities:
Hosts file on the SSTP VPN client:
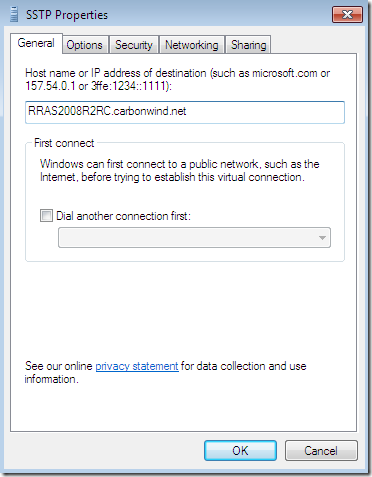
Configured VPN connection on the client:
We can make the 0x80092013 CRL check error “go away” without disabling the CRL check, if we download and import on the Windows 7 RC SSTP VPN client the latest base CRL and the latest delta CRL from our Enterprise CA that issued the certificate(obviously if you want to experiment a more “production like lab”-as production it can be a RC-, you should publish the required CRL distribution point and appropriately configure the VPN server’s certificate).
For example, initially establish a PPTP VPN connection from your client, and while you download the needed CA’s certificate from the Web enrollment site on the CA, also download the latest base CRL and the latest delta CRL:
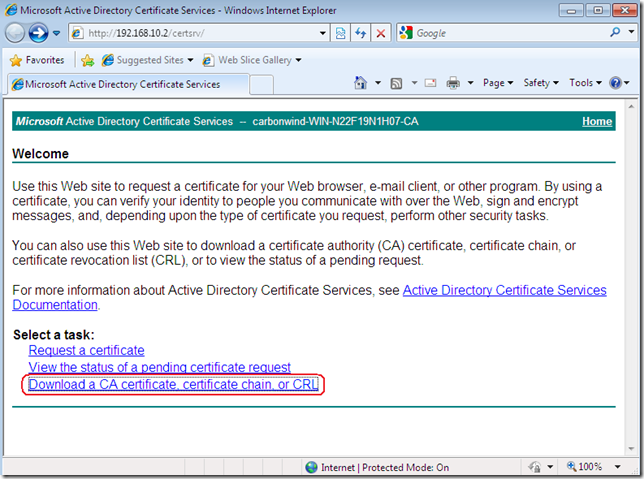
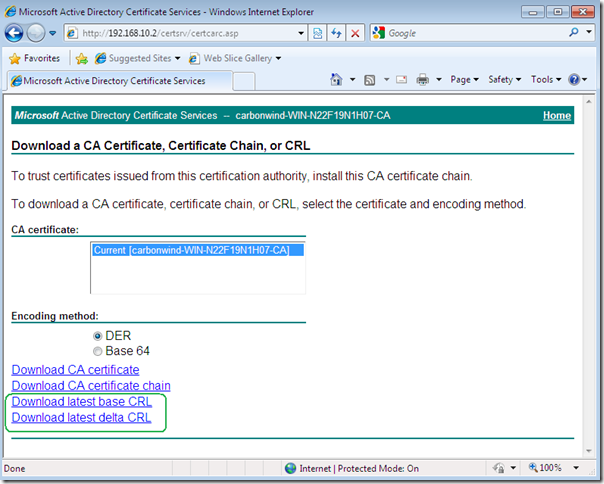
Then, after you’ve imported on the client the CA’s certificate within the Certificates Computer Store, Trusted Root Certificates Authorities, import the latest base CRL and the latest delta CRL into the Certificates Computer Store, Intermediate Certificates Authorities:
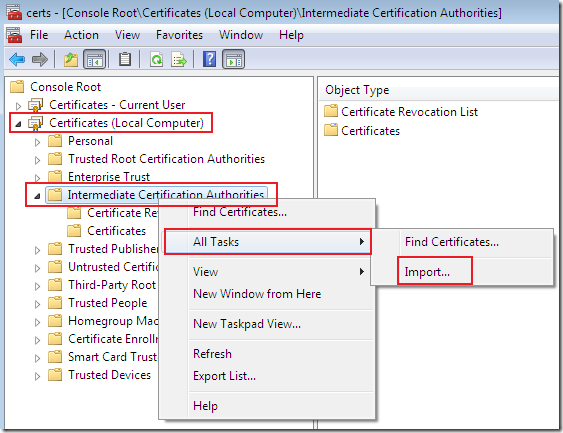
Just follow the wizard:
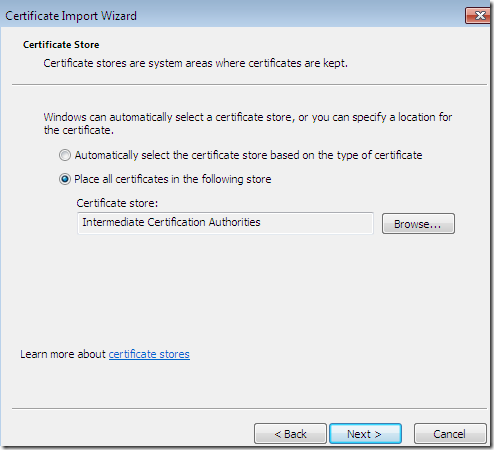
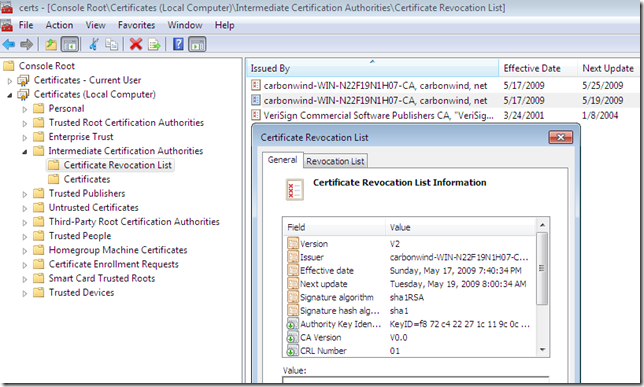
After you import them, they will appear within the Certificates Computer Store, Intermediate Certificates Authorities, Certificate Revocation List:
- base CRL:
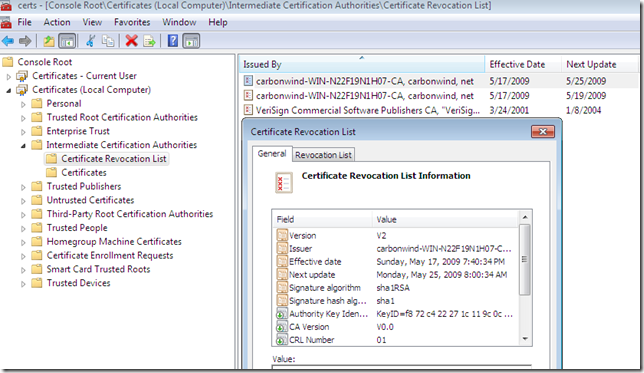
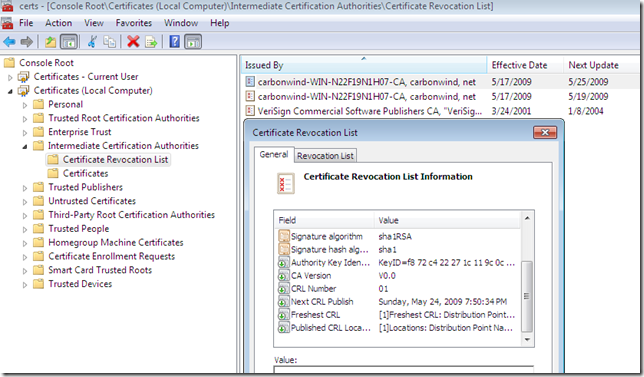
- delta CRL:
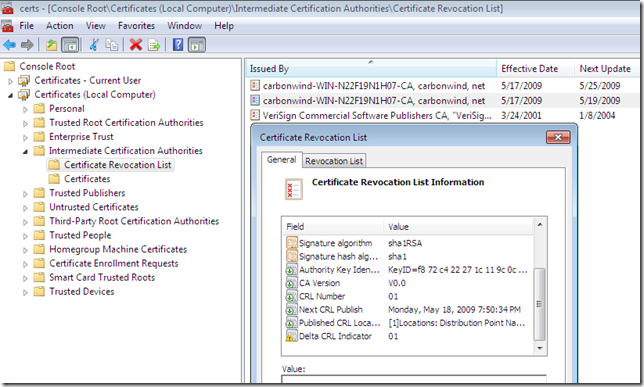
And now you should be able to establish your SSTP connection from the Windows 7 RC VPN client(EAP-MSCHAPv2 was used bellow for user authentication):
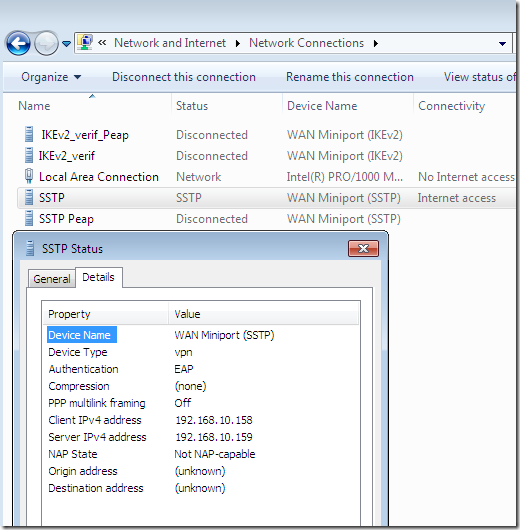
Related documents:
- How to debug SSTP specific connection failures:
http://blogs.technet.com/rrasblog/archive/2007/09/26/how-to-debug-sstp-specific-connection-failures.aspx
- How to troubleshoot Secure Socket Tunneling Protocol (SSTP) based connection failures when client fails to connect to SSTP VPN server giving error message 0x80092013”
http://support.microsoft.com/kb/961880
- How to troubleshoot Secure Socket Tunneling Protocol (SSTP)-based connection failures in Windows Server 2008:
http://support.microsoft.com/kb/947031
- Revoking certificates and publishing CRLs:
http://technet.microsoft.com/en-us/library/cc782162.aspx
- Schedule the publication of the certificate revocation list:
http://technet.microsoft.com/en-us/library/cc781735(WS.10).aspx