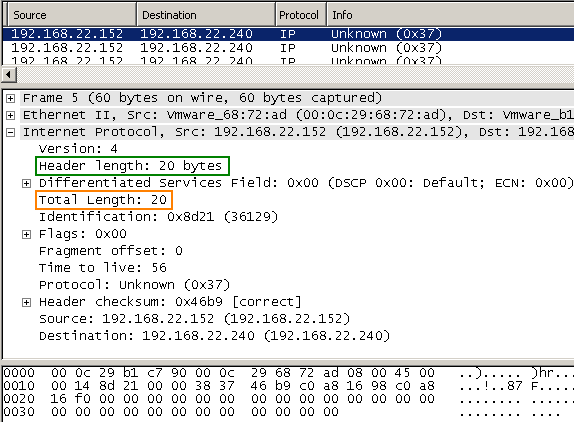
Just for the record:
If you have ever sent to your ISA Server 2004/2006 or attempted to sent through your ISA an IP packet that consists of only an IP header, you may have noticed that your ISA logs do not show anything.
Here is the explanation why:
http://support.microsoft.com/kb/936905
Windows Server 2003 simply drops those packets, without forwarding them to ISA.
These packets do not pass through ISA or if they target one of ISA's IP addresses, there is no reply packet, they are silently dropped, so there is nothing to worry about.
But you'll never know that someone made some "funky" attempts, assuming that you may want to know.
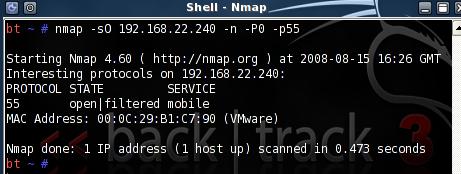
Bellow is the nmap command, just in case you want to test it yourself(-p55 means IP Protocol 55, will set the Protocols field within the IP header, I've entered a random number).
Note that if you use -p6 which means TCP, nmap will send an ACK segment to a random destination port.
Also if you use -p17 which means UDP, nmap will send an UDP packet to a random destinaton port.
And if you use -p255, and the destination host is on the local network, nmap will first send an ARP request for the destination IP address, and if an ARP reply is received, the IP packet that consists of only an IP header will be sent to the specified destination. If you replace the host destination with the entire local network, say 192.168.22.0/24, nmap will first send an ARP request for the every IP address from the specified network range, and for every host that sends an ARP reply, the IP packet that consists of only an IP header will be sent.
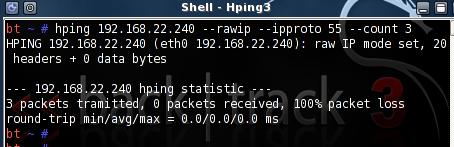
Or the hping3 command(--iproto 55 means IP Protocol 55, will set the Protocols field within the IP header):
Such a packet captured with Wireshark: