Note: The registry settings modified bellow are not currently publicly documented by Microsoft(at least according to my knowledge). I’m not sure if this is a supported configuration or not.
As we discussed here, IE8 on Windows 7 using TLS 1.2 does not append to its Client Hello message within the TLS 1.2 signature_algorithms extension the sha512/ecdsa combo('\x06\x03’ value). This extension is used to indicate to the server which signature/hash algorithm pairs may be used in digital signatures.
As a result IE8 might be unable to connect using TLS 1.2 say to an IIS 7.5(Windows Server 2008 R2) secure web server using a certain certificate, say an ECC certificate signed with SHA512ECDSA:
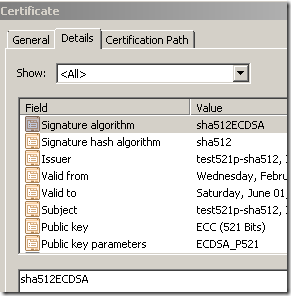 or
or 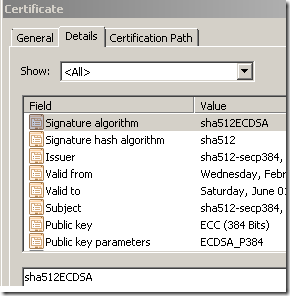
Note: IE8 is able to connect using TLS 1.0 or TLS 1.1 to a server using a certificate like above.
IE8 on Windows 7 Client Hello message original signature_algorithms extension vs modified signature_algorithms extension:
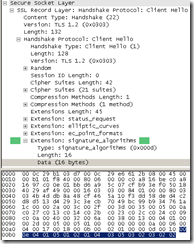 vs
vs 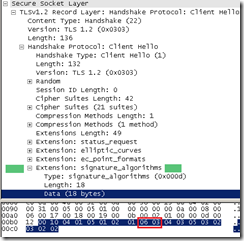
When I wrote the linked above blog entry I did not figure it how to make IE8 on Windows 7 append this combo to the signature_algorithms extension, today, as can be seen from above, I did figure it, heh, it took me less than a minute. :)
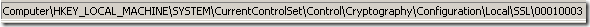
The secret seems to be within the Functions registry entry found at:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Cryptography\Configuration\Local\SSL\00010003
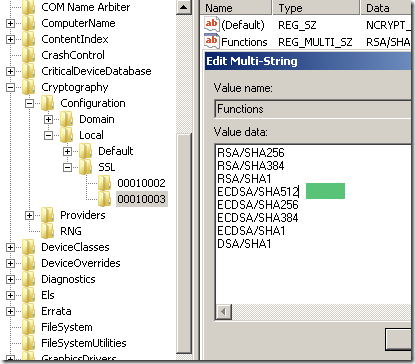
As can be seen from above I’ve added the ECDSA/SHA512 value to this registry entry(if you want you can add RSA/SHA512 too, I did no try this yet).
Reboot the machine after you make the modifications.
If you want to use P_521 cipher suites, such cipher suites are not enabled by default on Windows 7.
IE8 on Windows 7 Client Hello message original supported elliptic curves extension vs modified supported elliptic curves extension(look after secp521r1 (aka NIST P-521; value 25 = ‘0x0019’ in the supported elliptic curves extension extension) -TLS 1.2 Client Hello bellow, the supported elliptic curves extension is also used with TLS 1.0 and TLS 1.1-:
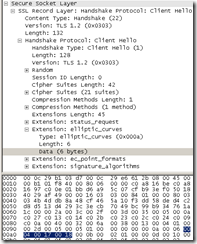 vs
vs 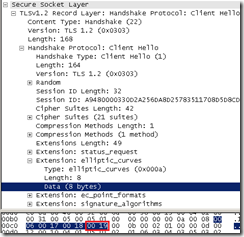
You can use the SSL Configuration Settings group policy to enable P_521 cipher suites or, use the Functions registry entry found at:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Cryptography\Configuration\Local\SSL\00010002
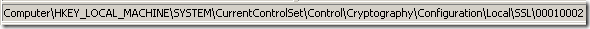
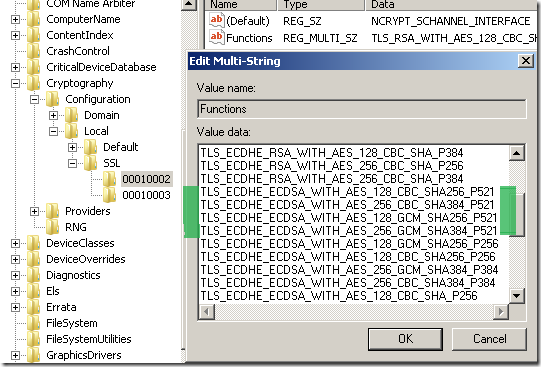
As can be noted above I’ve added a few P_521 cipher suites to the list.
Reboot the machine after you make the modifications.
Note: Although some NULL cipher suites might be listed as enabled either in the group policy or within the registry value from above, IE8 on Windows 7 or IIS 7.5 on Windows Server 2008 R2 do not use such cipher suites by default.