While looking the other days with Wireshark on Google Chrome 4 Beta’s TLS Client Hello message on Mac OS X, I’ve noticed that, by default, Anon and NULL encryption ciphers suites are listed as apparently supported cipher suites by Chrome.
On Mac OS X 10.5.8:
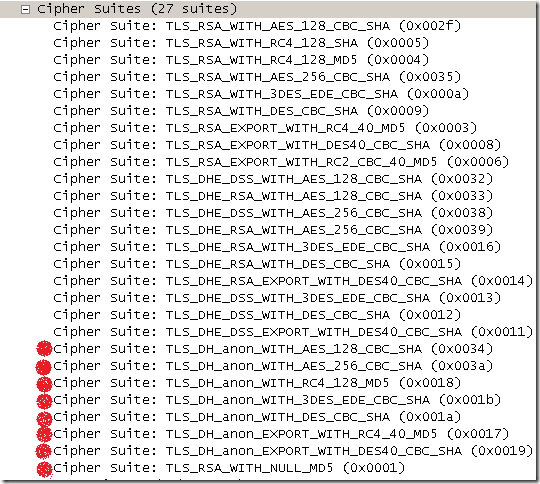
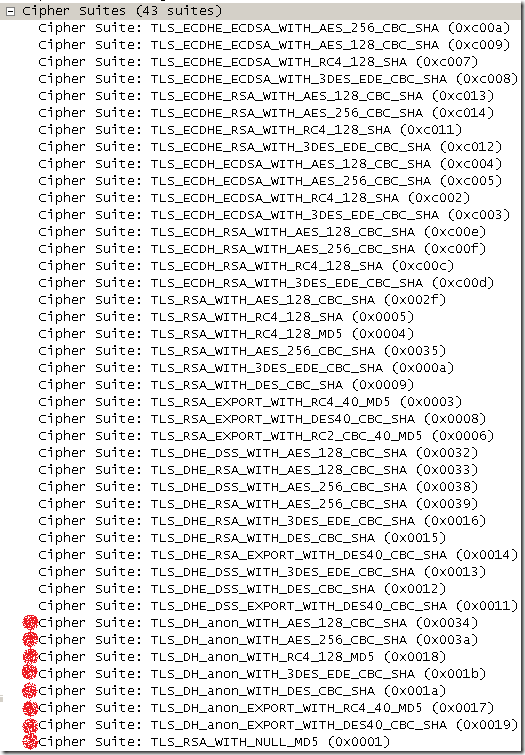
On Mac OS X 10.6.2:
Chrome version used:

The Anon ones are pretty dangerous, as a MITM attack is trivial to execute assuming the attacker has access to the “wire”.
Quickly attempting to use them against a test server, and, fortunately, apparently they do not seem usable.
Chrome negotiates and then closes the session.
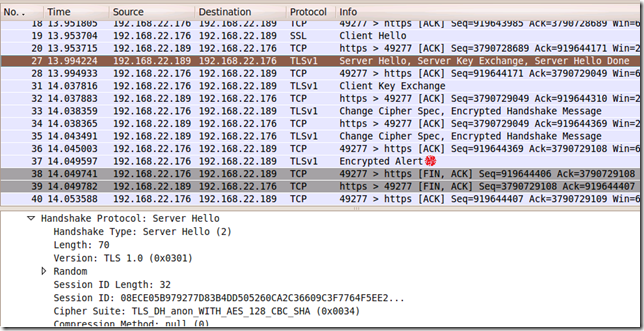
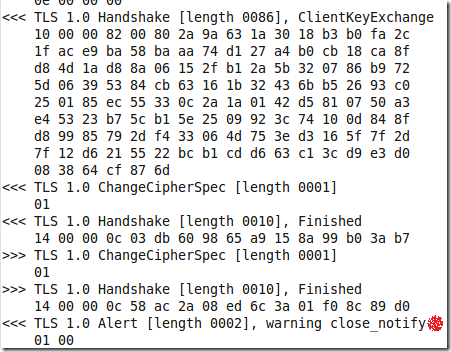
However, the NULL encryption one is usable. Chrome does not warn if there is no encryption between it and the server for the SSL/TLS session. You can view this aspect if you click on the padlock, but anyway few people do so.
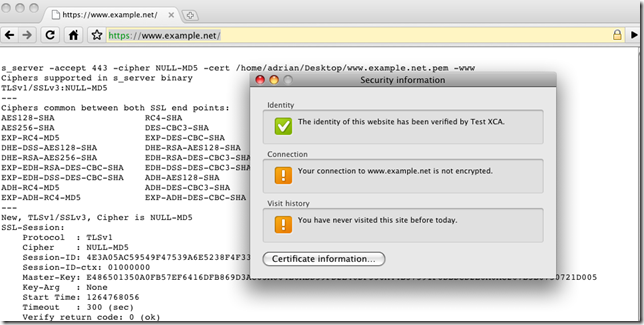
As a side note, as we saw from above, weak cipher suites are enabled too, Chrome does not warn if weak encryption is used between it and the server. You can view this aspect if you click on the padlock.
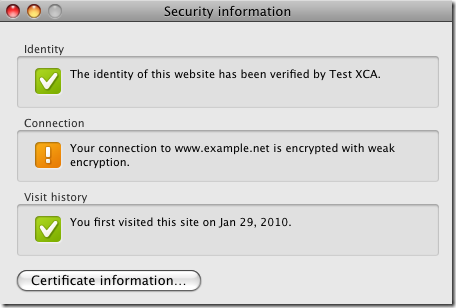
Weak encryption is possible on other platforms too, like Windows XP SP3, as Chrome(if installed on Windows) makes use of the Windows Schannel, and by default on Windows XP SP3 weak cipher suites are enabled. As a difference, Chrome was beta on Mac OS X, but on Windows the final version was used.
So, depending on the OS on which you installed Chrome, only “proper” cipher suites might or not might be enabled by default. Looks fine on Windows Vista SP2, Windows 7 and Linux(beta, Ubuntu 9.1 and Debian 5.0.3 x64 tested, NSS is used on Linux by Chrome).