|
23.08.2011
Vyatta Core 6.3 - Advanced VPN Site-to-Site Connections - Part 13 - Configure GRE/IPsec Between a Vyatta Router and a Cisco Router running Cisco IOS Using IPsec ESP in Transport Mode
1. Intro
2. Configuration Example
1. Intro
In the previous part we configured a GRE tunnel protected by IPsec tunnel mode between Vyatta and Cisco routers.
In this article we will establish a GRE tunnel between a Vyatta router(Core 6.3) and a Cisco router(2691 model, IOS version 124-25c), and use IPsec ESP transport mode to protect the GRE tunnel, thus to obtain a VPN.
We will also run OSPF(multicast) over the GRE tunnel to dynamically discover the networks behind the two routers.
This is a classic scenario made possible by the IPsec improvements in the Vyatta Core 6.3; we don't need anymore loopback interfaces.
A pre-shared key will be used for IKE MM authentication.
2. Configuration Example
Figure1 shows the network diagram for this lab:
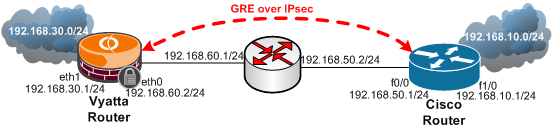
Figure1: Network Diagram
Note that only the IP addresses from Vyatta's eth0 interface and Cisco's f0/0 interface are considered to be public IP addresses within the below configuration; the IP addresses from these interfaces serve as IPsec VPN endpoints.
The below example only covers basic features. Please refer to each vendor's documentation for further details.
Vyatta Core's documentation can be found here.
You can search for your specific Cisco router model at Cisco's web site (Cisco has a "habit" from moving and re-moving documents on its web site, so I will avoid posting links that sooner or later may cease to exist).
|
user@router:~$ ----> user@router#
(from Operational Mode to Configuration Mode)
configure
|
router# ----> router(config)#
(from Privileged Mode to Configuration Mode)
configure terminal
|
|
Configure the ethernet interfaces:
set interfaces ethernet eth0 address 192.168.60.2/24
set interfaces ethernet eth1 address 192.168.30.1/24
commit
|
Configure the ethernet interfaces:
interface f0/0
ip address 192.168.50.1 255.255.255.0
exit
interface f0/1
ip address 192.168.10.1 255.255.255.0
exit
|
|
Configure a default route:
set protocols static route 0.0.0.0/0 next-hop 192.168.60.1
commit
|
Configure a default route:
ip route 0.0.0.0 0.0.0.0 192.168.50.2
|
|
Configure the tunnel interface:
edit interfaces tunnel tun1
set address 192.168.200.2/30
set encapsulation gre
set local-ip 192.168.60.2
set remote-ip 192.168.50.1
set multicast enable
top
commit
|
Configure the tunnel interface:
interface Tunnel0
ip address 192.168.200.1 255.255.255.252
tunnel source 192.168.50.1
tunnel destination 192.168.60.2
exit
|
|
Protect the GRE tunnel with IPsec.
Enable ipsec vpn on the desired interface:
set vpn ipsec ipsec-interfaces interface eth0
Specify the IKE MM Policy:
edit vpn ipsec ike-group ciscoike proposal 1
set encryption aes128
set hash sha1
set dh-group 5
top
set vpn ipsec ike-group ciscoike lifetime 28800
Specify the IKE QM Policy:
edit vpn ipsec esp-group ciscoesp proposal 1
set encryption aes128
set hash sha1
top
set vpn ipsec esp-group ciscoesp pfs enable
set vpn ipsec esp-group ciscoesp lifetime 3600
set vpn ipsec esp-group ciscoesp mode transport
Create a vpn ipsec site-to-site for the remote peer,
specifying the authentication method, the IKE MM and
QM policies to be used and the traffic to be protected:
edit vpn ipsec site-to-site peer 192.168.50.1
set authentication mode pre-shared-secret
set authentication pre-shared-secret 12345
set ike-group ciscoike
set local-ip 192.168.60.2
edit tunnel 1
set esp-group ciscoesp
set tunnel 1 protocol gre
top
commit
|
Protect the GRE tunnel with IPsec.
Specify the ISAKMP Policy:
crypto isakmp policy 25
hash sha
encr aes 128
group 5
lifetime 28800
authentication pre-share
exit
Match the remote peer with its pre-shared secret:
crypto isakmp key 12345 address 192.168.60.2
Specify the IKE QM Policy:
crypto ipsec transform-set vyattaset esp-aes 128 esp-sha-hmac
mode transport
exit
Define with a crypto ACL the protected traffic:
access-list 101 permit 47 host 192.168.50.1 host 192.168.60.2
Bind with a crypto map all the crypto parameters with the remote gateway:
crypto map vyatta 50 ipsec-isakmp
set peer 192.168.60.2
set transform-set vyattaset
match address 101
set pfs group5
exit
Apply the crypto map to the desired interface:
interface f0/0
crypto map vyatta
exit
|
|
Configure OSPF:
edit protocols ospf area 0
set network 192.168.30.0/24
set network 192.168.200.0/30
top
set protocols ospf log-adjacency-changes
commit
|
Configure OSPF:
router ospf 10
log-adjacency-changes
network 192.168.10.0 0.0.0.255 area 0
network 192.168.200.0 0.0.0.3 area 0
exit
|
|
|
|
|
Show the running configuration:
show -all |
Show the running configuration:
router(config)# ----> router#
(from Privileged Mode to Configuration Mode)
exit
show run
|
|
Save the current configuration(the configuration will be
saved to the config.boot file if we do not specify another
file):
save |
Save the running configuration to the startup configuration
(running-config(DRAM) to startup-config(NVRAM)):
copy run start
|
|
Show the IKE MM and IPsec SAs.
user@router# ----> user@router:~$(from Configuration
Mode to Operational Mode)
exit
show vpn ike sa
show vpn ipsec sa
|
Show the IKE MM and IPsec SAs:
show crypto isakmp sa
show crypto ipsec sa
|
|
View IPsec VPN debug information:
show vpn debug
|
Enable IKE and IPsec debugging in IOS(disable it by
a "no" in front of the below commands):
debug crypto isakmp
debug crypto ipsec
|
|
View the routing table:
show ip route |
View the routing table:
show ip route
|
|
View various OSPF details:
show ip ospf
show ip ospf route
show ip ospf interface
show ip ospf interface tun1
|
View various OSPF details:
show ip ospf
show ip ospf route
show ip ospf interface
show ip ospf interface tunnel0
|
|
Test connectivity from the router itself:
/bin/ping -I 192.168.30.1 -c 4 192.168.10.1
|
Test connectivity from the router itself(use the extended
command):
ping
Protocol [ip]:
Target IP address: 192.168.30.1
Repeat count [5]:
Datagram size [100]:
Timeout in seconds [2]:
Extended commands [n]: y
Source address or interface: 192.168.10.1
Type of service [0]:
Set DF bit in IP header? [no]:
Validate reply data? [no]:
Data pattern [0xABCD]:
Loose, Strict, Record, Timestamp, Verbose[none]:
Sweep range of sizes [n]:
|
|