|
04.04.2011
Using XCA to configure the OpenVPN PKI part as an alternative to OpenVPN's easy-rsa
- 1. Intro
- 2. Using XCA
- 2.1 Using XCA: Create a new database
- 2.2 Using XCA: Create a new CA
- 2.3 Using XCA: Create the OpenVPN server certificate
- 2.4 Using XCA: Create an OpenVPN client certificate
- 2.5 Using XCA: Export the CA certificate
- 2.6 Using XCA: Export the server certificate
- 2.7 Using XCA: Export the server private key
- 2.8 Using XCA: Export the client certificate
- 2.9 Using XCA: Export the client private key
- 3. Using XCA: Generate the Diffie-Hellman parameters
- 4. Sample OpenVPN server configuration
- 5. Sample OpenVPN client configuration
1. Intro
In this paper we will use XCA to configure the OpenVPN PKI part as an alternative to OpenVPN's easy-rsa.
With XCA you can create a CA, sign server and client certificates, revoke server or client certificates, create a CRL or generate DH parameters; all from a GUI.
So you can view and manage with ease your OpenVPN PKI.
The certificates and their corresponding private keys are stored in a database, database that you can put it into a safe place and access when needed.
2. Using XCA
First download and install XCA(within this paper XCA 0.9.0 will be installed on Windows 7 SP1), you can obtain the setup file from:
http://sourceforge.net/projects/xca
As a test OpenVPN server/client, the OpenVPN 2.1.4 version was used
2.1 Using XCA: Create a new database
Open XCA and from the File menu click New Database, see Figure 1:
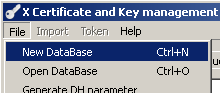
Figure1: XCA New Database
Save the database and enter a password used to encrypt the private keys, see Figure 2:
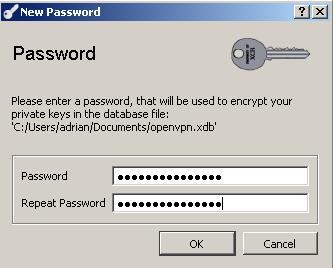
Figure2: XCA New Database - Enter Password
2.2 Using XCA: Create a new CA
Within the XCA GUI click the Certificates tab and click the New Certificate button, see Figure 3:
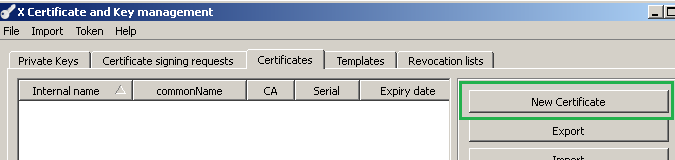
Figure3: XCA Database - New Certificate
On the Source tab we will select the CA template and click the Apply All button, see Figure 4:
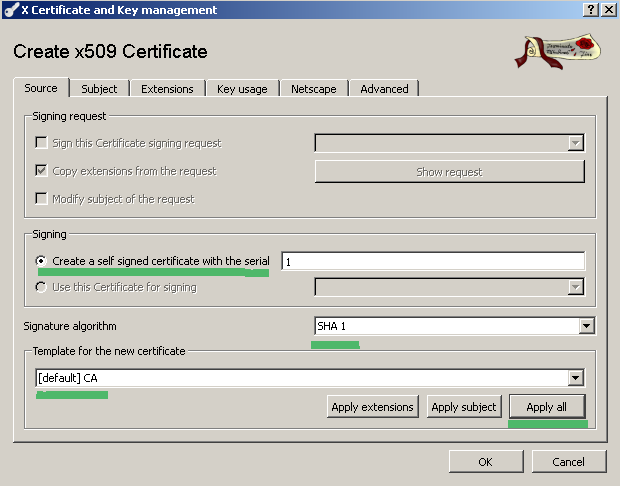
Figure4: XCA Database - New Certificate: Apply CA Template
On the Subject tab enter the certificate details(like CN, internal name(a name used to help you quickly identify a certificate), etc.), see Figure 5, and click the Generate a new key button in order to generate a new RSA key.
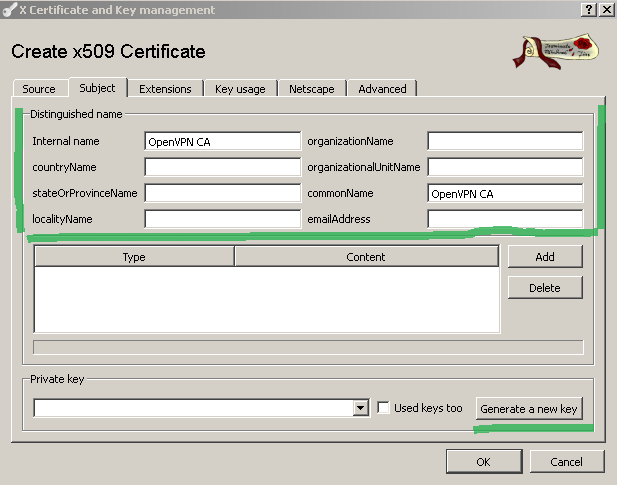
Figure5: XCA Database - New Certificate: Subject tab
Leave the Keytype to RSA, select the key size(2048 bit will be fine) and click the Create button, see Figure 6:
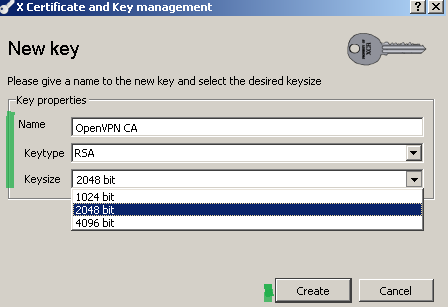
Figure6: XCA Database - New Certificate: Create a new RSA key for the CA
On the Extensions tab you can for example specify the CA certificate validity period, see Figure 7:
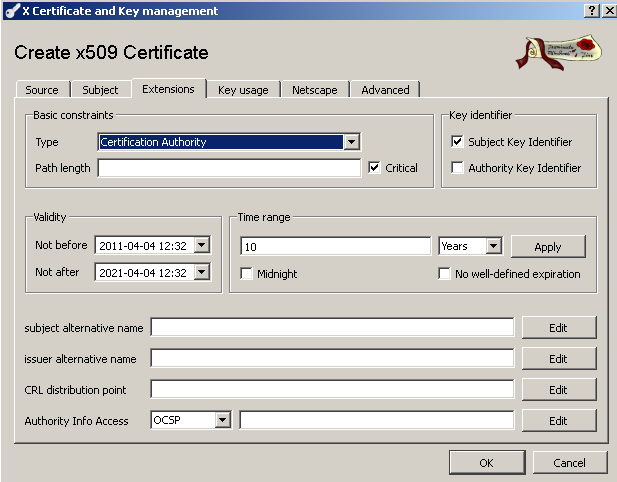
Figure7: XCA Database - New Certificate: Extensions tab
On the Key usage tab there isn't a particular need to change something, see Figure 8:
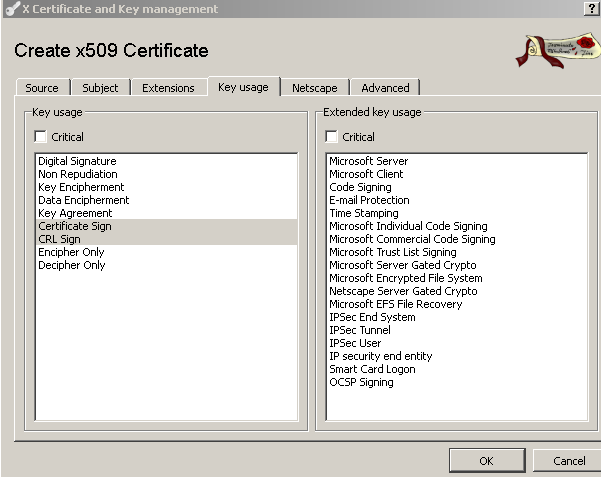
Figure8: XCA Database - New Certificate: Key usage tab
On the Netscape tab you can let selected the Netscape options, perhaps delete the Comment value, see Figure 9:
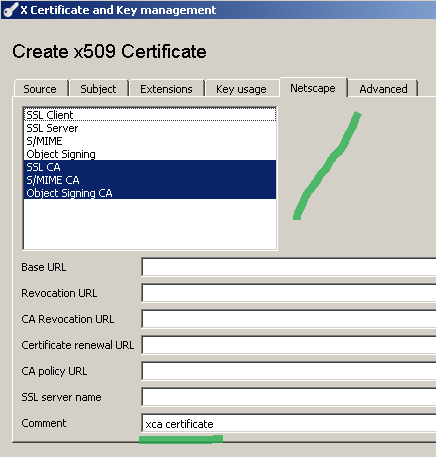
Figure9: XCA Database - New Certificate: Netscape tab
On the Advanced tab you can validate your settings.
Click the OK button to create the CA certificate.
And you've successfully created the CA which will be used to sign server and clients certificates, see Figure 10:
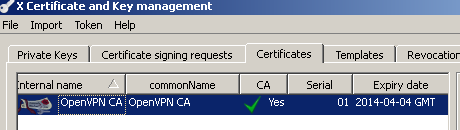
Figure10: XCA Database - CA certificate
2.3 Using XCA: Create the OpenVPN server certificate
Similar with the step from above for the CA certificate, within the XCA GUI click the Certificates tab and click the New Certificate button.
On the Source tab we will select the Use this Certificate for signing option and the created CA certificate; this time the HTTPS Server template will be used, click the Apply All button, see Figure 11:
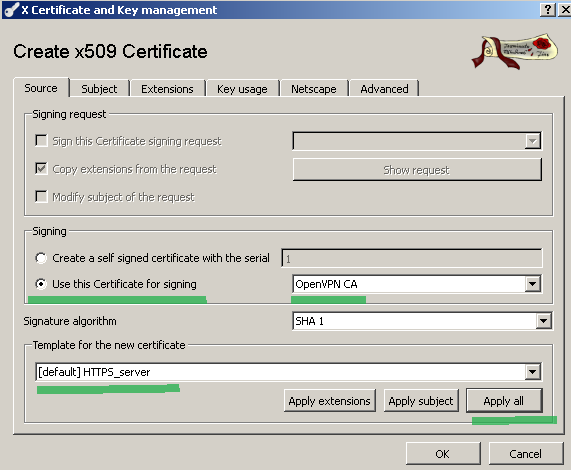
Figure11: XCA Database - New server certificate
On the Subject tab enter the certificate details(like CN, internal name(a name used to help you quickly identify a certificate), etc.), and as we did for the CA, generate a new RSA key(2048 bit will be fine) see Figure 12:
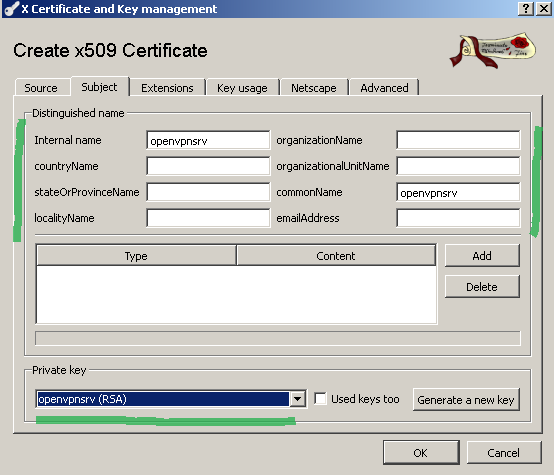
Figure12: XCA Database - New Certificate: Subject tab
On the Extensions tab you can for example specify the server certificate validity period, see Figure 13:
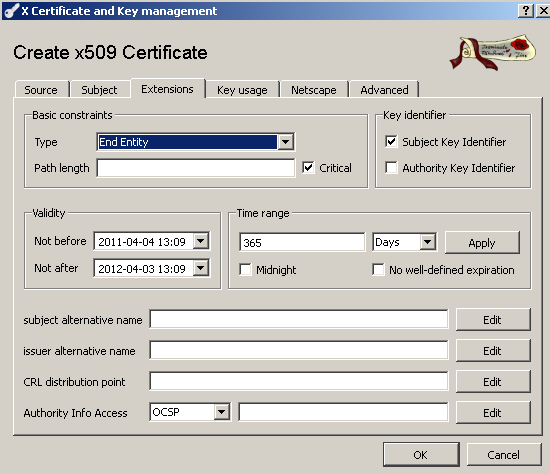
Figure13: XCA Database - New Certificate: Extensions tab
On the Key usage tab select the Microsoft Server EKU under the Extended key usage section and deselect Non Repudiation under the Key Usage section, see Figure 14:
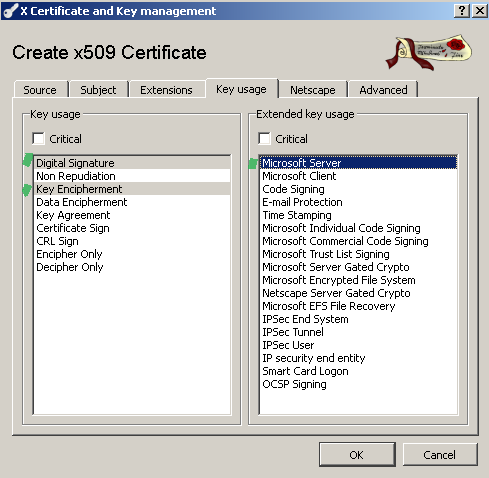
Figure14: XCA Database - New Certificate: Key usage tab
On the Netscape tab you can deselect the Netscape SSL Server option, and perhaps delete the Comment value, see Figure 15:
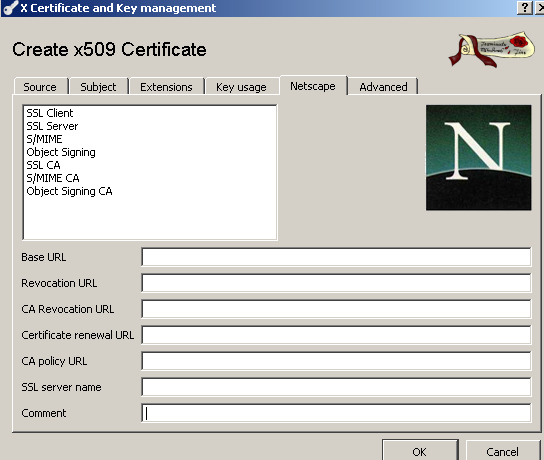
Figure15: XCA Database - New Certificate: Netscape tab
Note that we will not use the older option ns-cert-type server(that's why we don't need the Netscape server certificate type) nor the newer one remote-cert-tls server(for that we needed to set the Key Usage to Digital Signature and Key Encipherment without Non Repudiation) within the client config file; instead we will use the remote-cert-eku "TLS Web Server Authentication" option.
On the Advanced tab you can validate your settings.
Click the OK button to create the server certificate.
And you've successfully created the server certificate used on the OpenVPN server, see Figure 16, note that by default XCA orders the certificates in a tree view:
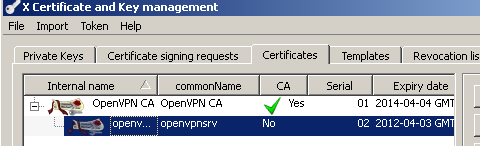
Figure16: XCA Database - server certificate
2.4 Using XCA: Create an OpenVPN client certificate
Similar with the step from above for the server certificate, within the XCA GUI click the Certificates tab and click the New Certificate button.
On the Source tab we will select the Use this Certificate for signing option and the created CA certificate; this time the HTTPS Client template will be used, click the Apply All button, see Figure 17:
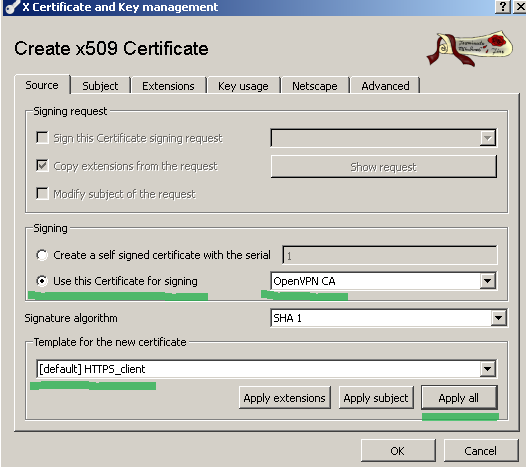
Figure17: XCA Database - New client certificate
On the Subject tab enter the certificate details(like CN, internal name(a name used to help you quickly identify a certificate), etc.), and as we did for the server, generate a new RSA key(2048 bit will be fine) see Figure 18:
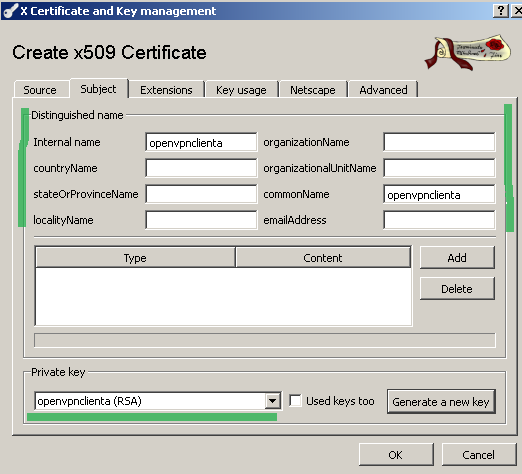
Figure18: XCA Database - New Certificate: Subject tab
On the Extensions tab you can for example specify the server certificate validity period, see Figure 19:
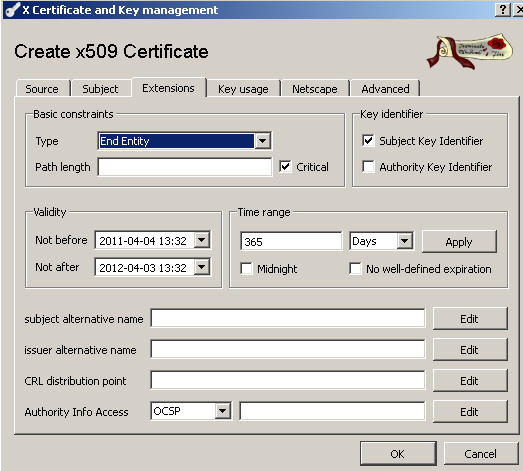
Figure19: XCA Database - New Certificate: Extensions tab
On the Key usage tab select the Microsoft Client EKU under the Extended key usage section; under the Key Usage section deselect Data Encipherment and Key Encipherment and select Key Agreement, see Figure 20:
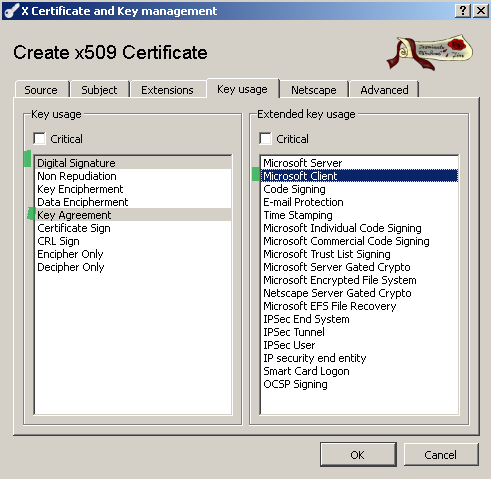
Figure20: XCA Database - New Certificate: Key usage tab
On the Netscape tab you can deselect the Netscape SSL Client and S/MIME options, and perhaps delete the Comment value, see Figure 21:
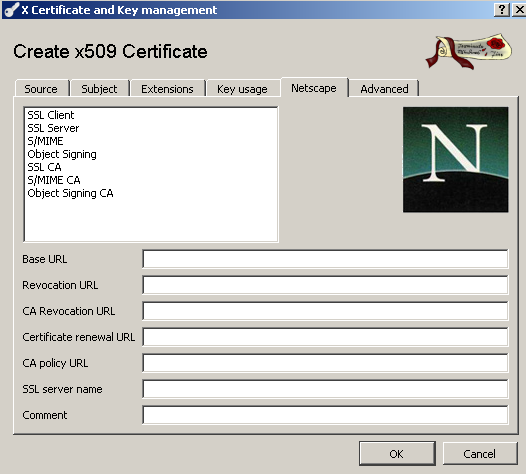
Figure21: XCA Database - New Certificate: Netscape tab
Note that we will not use the older option ns-cert-type client(that's why we don't need the Netscape client certificate type) nor the newer one remote-cert-tls client(for that we needed to set the Key Usage to Digital Signature and Key Agreement) within the server config file; instead we will use the remote-cert-eku "TLS Web Client Authentication" option.
On the Advanced tab you can validate your settings.
Click the OK button to create the client certificate.
And you've successfully created the client certificate used on the OpenVPN client, see Figure 22:
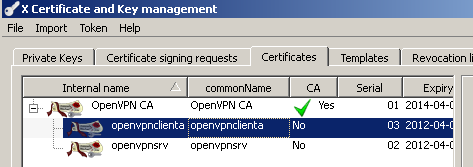
Figure22: XCA Database - client certificate
2.5 Using XCA: Export the CA certificate
On the server or clients we only need the CA certificate, not the associated private key.
Within the XCA GUI click the Certificates tab, select the CA certificate and click the Export button, see Figure 23:
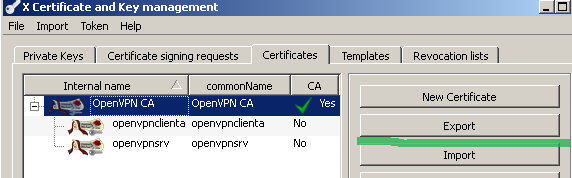
Figure23: XCA Database - exporting the CA certificate
Select PEM as the Export format, indicate the export location and click the OK button to export the certificate, see Figure 24:
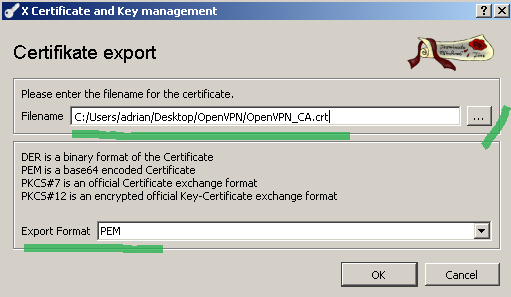
Figure24: XCA Database - export the CA certificate
For convenience I renamed the exported certificate's extension from .crt to .pem.
2.6 Using XCA: Export the server certificate
On the server we need the server certificate and the associated private key.
Within the XCA GUI click the Certificates tab, select the server certificate and click the Export button, see Figure 25:
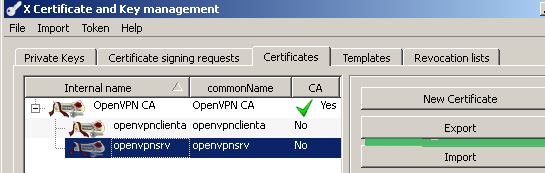
Figure25: XCA Database - exporting the server certificate
Select PEM as the Export format, indicate the export location and click the OK button to export the certificate, see Figure 26:
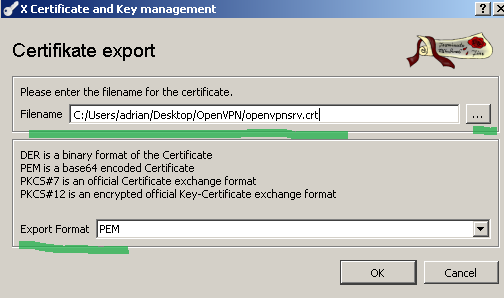
Figure26: XCA Database - export the server certificate
For convenience I renamed the exported certificate's from openvpnsrv.crt to openvpnsrv_cert.pem.
2.7 Using XCA: Export the server private key
As said, on the server we also need the server's private key.
Within the XCA GUI click the Private Keys tab, select the server private key and click the Export button, see Figure 27:
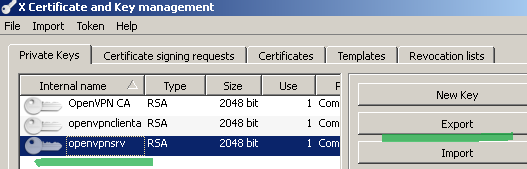
Figure27: XCA Database - exporting the server private key
Select PEM as the Export format, indicate the export location and click the OK button to export the private key, see Figure 28:
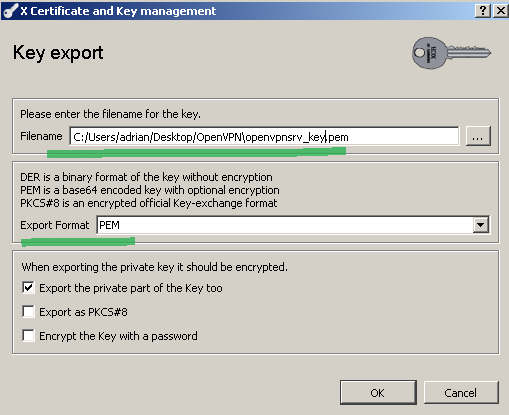
Figure28: XCA Database - export the server private key
Note that the private key is not encrypted, thus be careful with it.
Also the private key was exported using the PKCS#8 format, and not the traditional SSLeay compatible format.
You can spot the PKCS#8 format by opening the exported file with a text editor, it should be something like:
-----BEGIN PRIVATE KEY-----
MIIEvgIBADANBgkqhkiG9w0BAQEFAASCBK...
The traditional SSLeay compatible format will look like(opening the file with a text editor):
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAzCJqwrUlV21lS4vM/Y...
The PCKS#8 format may pose problems, for example, if you configure OpenVPN on Vyatta Core 6.2.
To walk around this issue, unfortunetely, I think, for now, you need to use the OpenSSL CLI(you need to install OpenSSL on your machine, if OpenVPN was installed on it, OpenSSL should be installed too) like so:
openssl rsa -in 'exportedXCAprivatekey' -out 'SSLeaycompatibleformat'
or like:
openssl pkcs8 -nocrypt -in 'exportedXCAprivatekey' -out 'SSLeaycompatibleformat'
To my current knowledge this should be fixed in the next XCA release.
2.8 Using XCA: Export the client certificate
On the client we need the client certificate and the associated private key.
Within the XCA GUI click the Certificates tab, select the client certificate and click the Export button, see Figure 29:
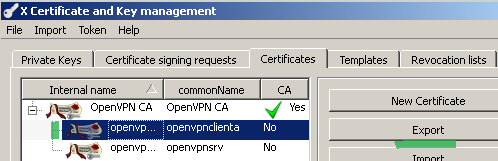
Figure29: XCA Database - exporting the client certificate
Select PEM as the Export format, indicate the export location and click the OK button to export the certificate, see Figure 30:
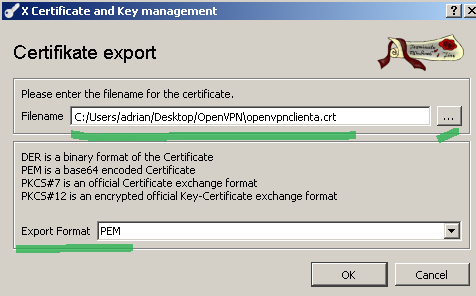
Figure30: XCA Database - export the client certificate
For convenience I renamed the exported certificate's from openvpnclienta.crt to openvpnclienta_cert.pem.
2.9 Using XCA: Export the client private key
As said, on the client we also need the client's private key.
Within the XCA GUI click the Private Keys tab, select the client private key and click the Export button, see Figure 31
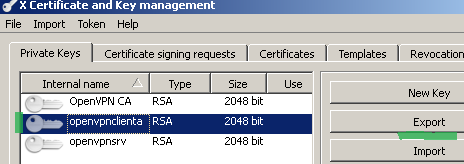
Figure31: XCA Database - exporting the client private key
Select PEM as the Export format, indicate the export location and click the OK button to export the private key, see Figure 32:
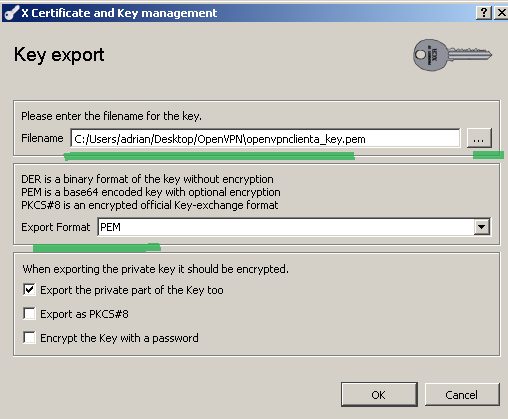
Figure32: XCA Database - export the client private key
Note that the private key is not encrypted, thus be careful with it.
Also, as in the server's case, the private key was exported using the PKCS#8 format, and not the traditional SSLeay compatible format.
3.0 Using XCA: Generate the Diffie-Hellman parameters
Now we need to generate the Diffie-Hellman parameters used on the server.
Within the XCA GUI from the File menu click the Generate DH parameter button, see Figure 33:
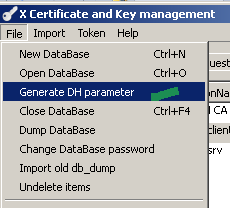
Figure33: XCA - Generate DH parameter option
We will generate 2048 bits DH parameter(the generator will be 2), so enter 2048 as the number of bits, see Figure 34:
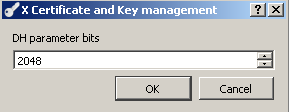
Figure34: XCA - Generate 2048 bit DH parameter
Click the OK button to create the Dh parameter, be patient as this will take some time, the XCA GUI may look like will not respond within this period of time.
When prompted indicate the saving location and click the OK button to save the generated DH parameter, see Figure 35:
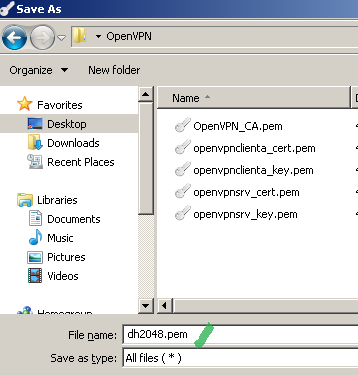
Figure35: XCA - Save 2048 bit generated DH parameter
4. Sample OpenVPN server configuration
Bellow there is a basic sample of an OpenVPN server configuration running in routing mode(note that we're not pushing any routes though):
Sample OpenVPN server configuration.
The OpenVPN server runs on Windows Server 2003 R2 SP2, note that we've placed the needed files(certs, key DH param, server configuration file) within the configuration folder, see Figure 36:
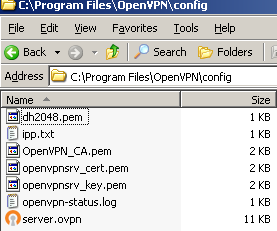
Figure36: OpenVPN server configuration folder
5. Sample OpenVPN client configuration
Bellow there is a basic sample of an OpenVPN client configuration running in routing mode:
Sample OpenVPN client configuration.
The OpenVPN client runs on Windows XP SP3, note that we've placed the needed files(certs, key, client configuration file) within the configuration folder, see Figure 37:
Figure37: OpenVPN client configuration folder
|