|
21.06.2007
Describing an alternative method to FTP over TLS by the use of WebDav over TLS published through ISA 2006 Firewall - Part 6 - User Certificate Authentication on ISA 2006 Firewall
Regarding the use of a user certificate as a strong authentication method(high security), we need a WebDav client supporting such an authentication method. And that might be a problem.
I had modified the WebDav rule (Web Listener Properties) to use "SSL Client Certificate Authentication". See Figure140.
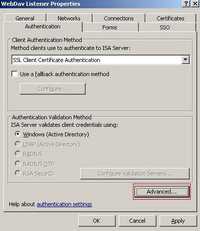
Figure140: SSL Client Certificate Authentication
In the "Advanced Authentication Options" I have specified the CA from which ISA trusts user certificates. See Figure141.
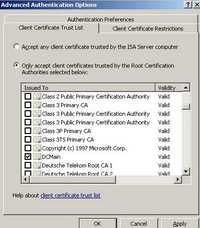
Figure141: Specify the CA From Which ISA Accepts User Certificates
Next we need a delegation method or allow the client to authenticate directly(not desired). Therefore as the delegation method, I have selected KCD(Kerberos Constrained Delegation). See Figure142. Without KCD, ISA Server can delegate credentials only when client credentials are received using Basic authentication or HTTP forms-based authentication. So KCD is a powerful feature of ISA 2006.
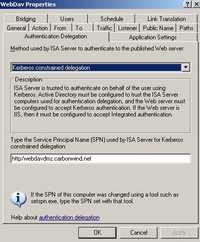
Figure142: Kerberos Constrained Delegation
The SPN (Service Principal Name) is not http/fileserver.carbonwind.net, is the host name on which IIS is installed(I do not have a host header on the web site), IIS runs under the Network Service account. Therefore the SPN is http/webdavdmz.carbonwind.net.
After ISA verifies the user's identity(through the SSL user certificate), ISA will obtain a Kerberos service ticket for authenticating the user to the WebDav server. When SSL user certificate is used for authentication, ISA cannot delegate the user's credentials to the WebDav server, because the client does not send to ISA a password that can be passed to the WebDav server. Also the SSL user certificate cannot be forwarded to the WebDav server because only the user has access to the private key corresponding to the public key present on the user certificate. ISA knows the user name from the user's certificate(SSL user certificates are mapped to Active Directory user accounts).
Thus, at the domain controller, within "Active Directory Users and Computers" we need to configure the webdavdmz server to trust the Kerberos ticket obtained on the behalf of the user by ISA (actually this is done on the ISAMAIN computer and not on the WEBDAVDMZ computer). See Figure143.
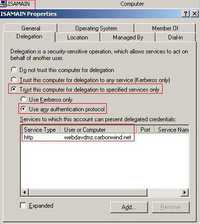
Figure143: ISA Computer Delegation Tab
Note that the Computer name from Figure143 matches the one from the SPN entered on ISA. Please refer to the following Microsoft doc regarding KCD in ISA: Kerberos Constrained Delegation in ISA Server 2006.
Using Internet Explorer, Firefox or Opera I can access the WebDav server with no problems (browse, download). See Figure144, Figure145 and Figure146.
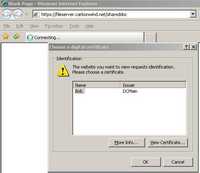
Figure144: Internet Explorer
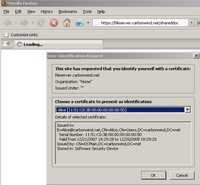
Figure145: Firefox
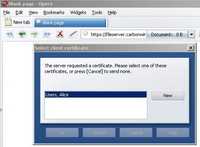
Figure146: Opera
Using the WebDav Windows XP built-in client also works(default install, with or without MS Office 2007 installed). Well, well, well. For sure it strikes back. When you are adding a Network Place you are prompted for a user certificate. See Figure147.
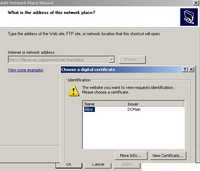
Figure147: Adding a Network Place
When you open the newly added Network Place you are prompted for a user certificate. See Figure148.
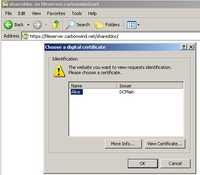
Figure148: Open the Newly Added Network Place
And success, see Figure149. No more worries about passwords strength. A powerful authentication method, requiring minimum effort from users(no more complaints about password complexity). The users only need to present a valid user certificate to ISA from the trusted CA.
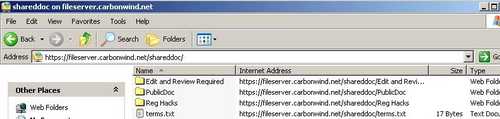
Figure149: Web Folders
And the corresponding ISA logs. See Figure150, Figure151, Figure152 and Figure153.
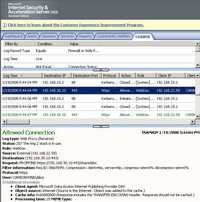
Figure150: ISA Log PROPFIND Request User Certificate Authentication + KCD
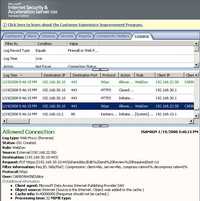
Figure151: ISA Log PUT Request User Certificate Authentication + KCD
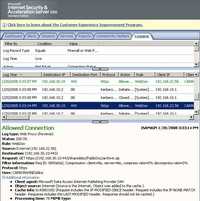
Figure152: ISA Log GET Request User Certificate Authentication + KCD
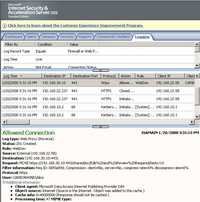
Figure153: ISA Log MOVE Request User Certificate Authentication + KCD
If you attempt to open a Word doc for example from Web Folders, you will be prompted for the user certificate. See Figure154.
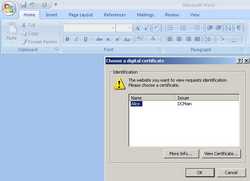
Figure154: Word Doc User Certificate Authentication + KCD
And some ISA logs for that attempt, see Figure155 and Figure156.
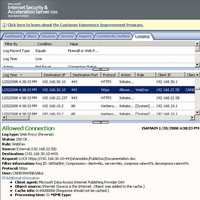
Figure155: ISA Log LOCK Request User Certificate Authentication + KCD
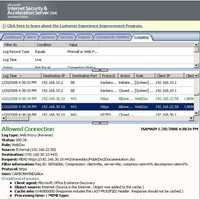
Figure156: ISA Log HEAD Request User Certificate Authentication + KCD
WebDrive let us use client certificates. It has a certificate manager, so we can import certificates. See Figure157.
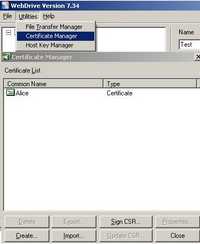
Figure157: WebDrive Certificate Manager
And then specify within the Properties of the Site the client certificate to be used. See Figure158.
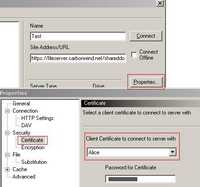
Figure158: WebDrive Client Certificate
However WebDrive is unable to connect. Wireshark traces and ISA's logs show that the SSL authentication succeeds but WebDrive fails with some cryptic error(see bellow).
"Connecting securely to https://fileserver.carbonwind.net/shareddoc:443 ...
Connecting to port 443
Encryption handshake successful
OPTIONS /shareddoc HTTP/1.1
req: Host: fileserver.carbonwind.net:443
User-Agent: WebDrive 7.34.1801 DAV
req: Translate: f
req: Content-Length: 0
req: Connection: Keep-Alive
ReceiveLine: encrypted read error=recv() failed in crypto layer (Error 1506)
HTTP Connection closing
Retrying HTTP command
Connecting to port 443
Encryption handshake successful
OPTIONS /shareddoc HTTP/1.1
req: Host: fileserver.carbonwind.net:443
req: User-Agent: WebDrive 7.34.1801 DAV
req: Translate: f
req: Content-Length: 0
req: Connection: Keep-Alive
ReceiveLine: encrypted read error=recv() failed in crypto layer (Error 1506)
HTTP Connection closing
Request failed: -1
Failed to connect to Site Test at https://fileserver.carbonwind.net/shareddoc, error=Request failed: -1 , LogonFailure=0"
And the corresponding ISA logs, see Figure159. ISA logs a sucessful attempt(200 OK), the same sucessful attempt can be seen in IIS logs.
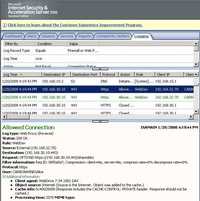
Figure159: ISA Log WebDrive User Certificate Authentication + KCD
I did not notice an option on Total Commander WebDav plugin or on CentOS 4.4(although Neon seems to support client certificates) to specify a client certificate.
As can be seen, with the proper WebDav client this is the way to go in implementing a strong authentication method. At the end of the day, it's not an ISA problem, only a WebDav client one.
In Part 7 we will provide a quick explanation of WebDav through ISA 2006 Firewall.
|