|
30.08.2007
Creating a site-to-site VPN partial mesh architecture with ISA 2006 Firewall Standard Edition
- 1. Overview
- 2. Configure ISAA - The connection to ISAB
- 3. Configure ISAA - The connection to ISAC
- 4. Add the Users Branch and Branch2 on ISAA
- 5. Configure ISAB - The connection to ISAA
- 6. Configure ISAB - The connection to ISAC
- 7. Add the Users Main and ToBranch2 on ISAB
- 8. Configure ISAC - The connection to ISAA
- 9. Configure ISAC - The connection to ISAB
- 10. Add the Users Main1 and ToBranch on ISAC
- 11. Test the s2s Connections
1. Overview
Let's assume that you have three different locations, LocationA, LocationB and LocationC. LocationA, LocationB and LocationC are protected using ISA 2006 Firewalls Standard Edition. Each location has one Internet connection.
You would like to connect all the locations togheter.
So you think on using site-to-site VPN connections. You have opted for L2TP/IPsec connections.
There is a site-to-site VPN connection between LocationA and LocationB.
There is a site-to-site VPN connection between LocationA and LocationC.
There is a site-to-site VPN connection between LocationB and LocationC.
So every location has two site-to-site VPN connections.
Bellow is the network diagram.
SiteA IP address range: 192.168.10.0/24
SiteB IP address range: 192.168.40.0/24
SiteC IP address range: 192.168.50.0/24 It is not a full mesh topology because if, say, the site-to-site VPN connection betweenLocationA and LocationB is down, traffic will not be directed from LocationA to LocationBthrough LocationC. But since you have only one Internet connection, there is no redundant path if your Internet connections goes down. Also if the site-to-site VPN connection betweenLocationA and LocationB is down and there is an ISA problem then, very likely that the other site-to-site VPN connection between LocationA and LocationC will be down too. If you really want redundancy then you need multiple machines and Internet connections to achieve it.
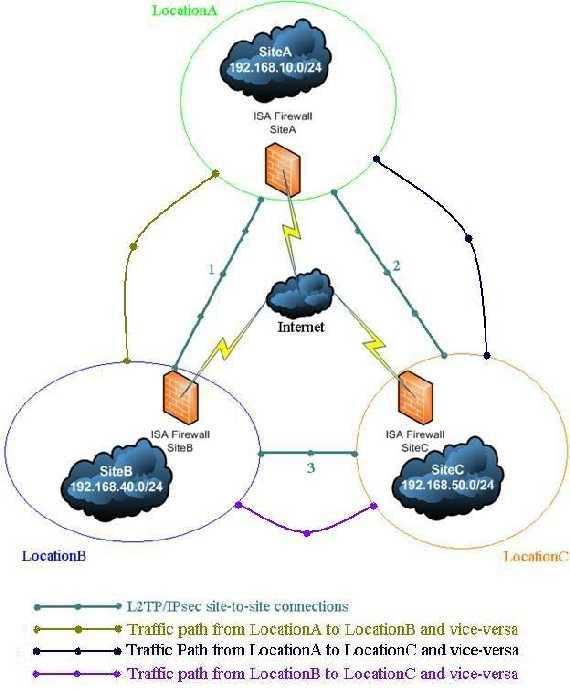
Figure1: The Network Diagram
So let’s proceed.
2. Configure ISAA - The connection to ISAB
First the ISA machine from LocationA.
As said before we need to create two site-to-site VPN connections using L2TP/IPsec.
ISA can play the role of the Calling Gateway or the Answering Gateway. Suppose that a client from SiteB wants to connect to a computer from SiteA. Since the tunnel is not up yet, whenISAB at the SiteB will receive the client request will try to initiate the connection. In this wayISAB is acting as the Calling Gateway. Obviuosly ISAA(domain member) will be the Answering Gateway. Remember that L2TP/IPsec requires two level of authentication: machine(through IKE) and user(PPP authentication). So we need to configure ISAB with a user name and password that are available at the ISAA location, user which has “Dial-in” permissions set to allowed. Even more, the user name must match the remote site name fromISAA.
Using the site-to-site wizard we are going to create on ISAA the connection to ISAB, We'll name it Branch.
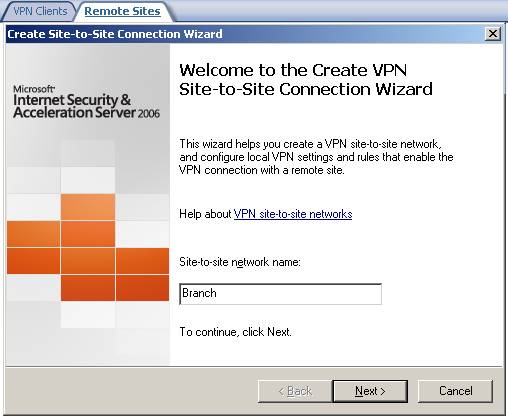
Figure2: Site-to-site wizard on ISAA adding the connection to ISAB
Choose L2TP/IPsec:
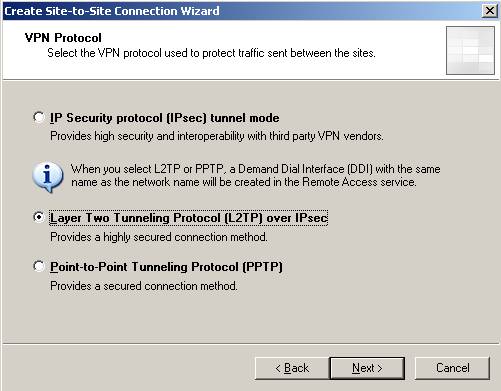
Figure3: Choosing L2TP/IPsec
We receive the user warning that I have told you about:
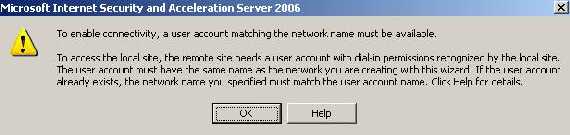
Figure4: User account warning
Enter the remote site address(it can be an IP address or a FQDN):
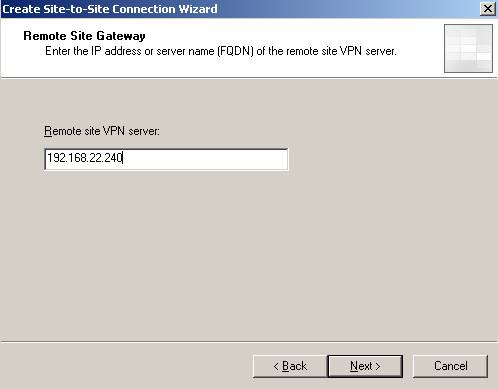
Figure5: The Remote site VPN server
You can configure ISAA to act as the Calling Gateway for this connection(at least one side must be configured to do so). We’ll name the user Main. If you want that only ISAB to initiate the connection to ISAA uncheck the checkbox:
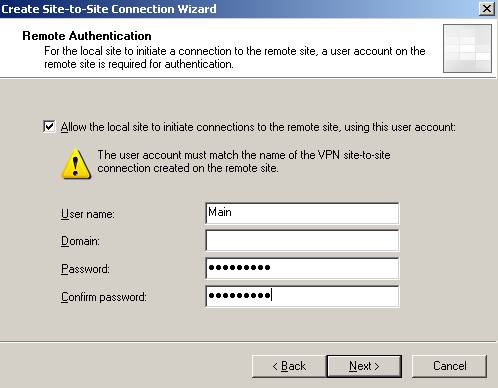
Figure6: Allow ISAA to act as the Calling Gateway
Next we need to specify the outgoing authentication method for IKE when ISAA is acting as the Calling Gateway. Make sure you use certificates and not pre-shared key in a production environment. Right now I’m going to use a pre-shared key.
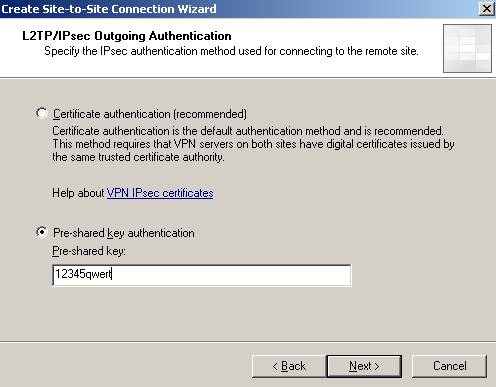
Figure7: IKE authentication when ISAA acts as the Calling Gateway
If you did not enable “VPN Client Access” and there specified for example a pre-shared key you will be prompted by ISA to define an authentication method for incoming connections.
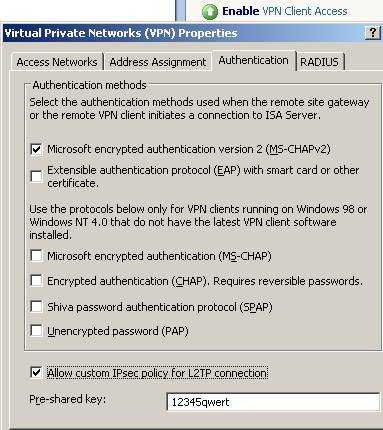
Figure8: Enable VPN Client Access
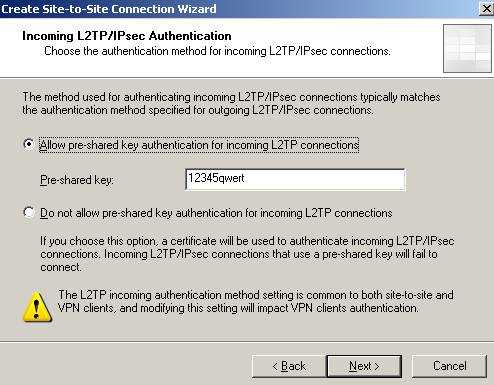
Figure9: Incoming connections Authentication method
If ISAA is the Answering Gateway and you are using pre-shared keys make sure you add a pre-shared key.
I know is weird, but actually the Calling Gateway is "acting" like a "VPN client" and therefore if you use pre-shared keys on the Answering Gateway for VPN clients too, then everybody(Calling Gateways and VPN clients) will use the same pre-shared key. Keep in mind that there are separate System Policies enabled for you by ISA(when you click “EnableVPN Client Access” or define a site-to-site VPN) for VPN clients and site-to-site connections so you do not need to create any access rules or whatever.

Figure10: System Policy VPN client access enabled(PPTP and L2TP/IPsec)
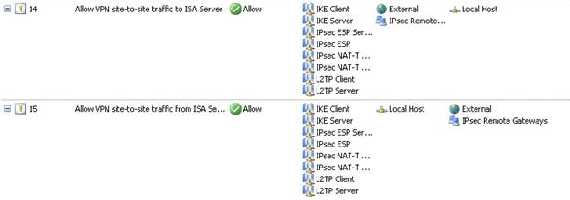
Figure11: System Policy VPN site-to-site enabled
Add the remote site IP address range:
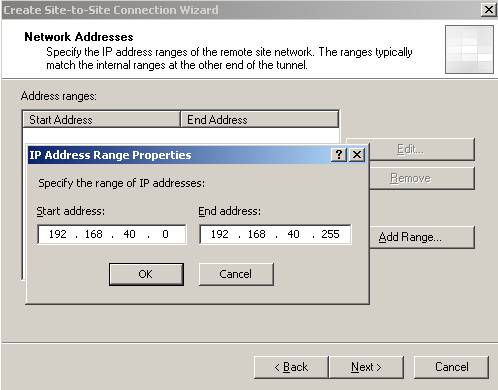
Figure12: Remote site IP address range
Next create a network rule between the new remote site and your Internal Network(a route relationship):
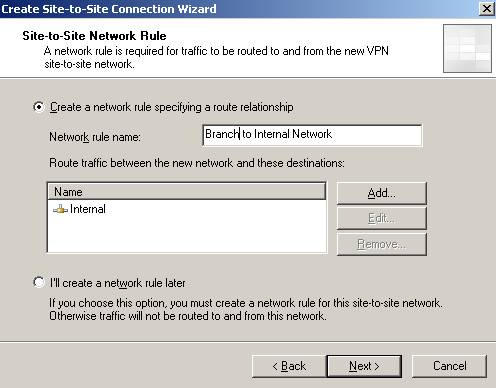
Figure13: The network relationship
And the access rules for allowing communications between Branch and Internal and vice-versa. Right now I have defined an allow all rule.
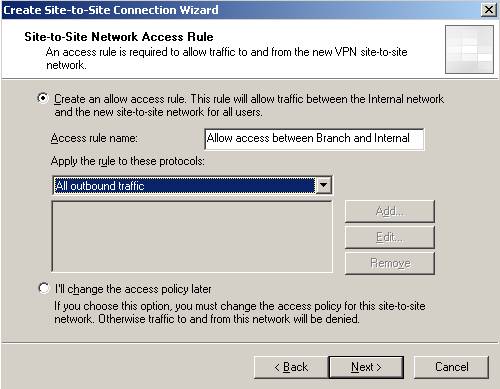
Figure14: The access rule
And then click “Finish”.
So by now you should have the System Policies enabled, the access rules and the network relationship(route) defined:

Figure15: Access rule between Branch and Internal and vice-versa

Figure16: Network rule between Branch and Internal
Now head onto RRAS and make sure you uncheck the “Register this connection’s addresses in DNS” on the “Branch” interface:
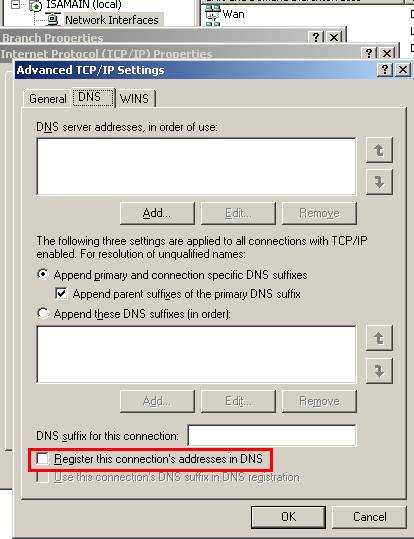
Figure17: Uncheck the “Register this connection’s addresses in DNS”
If you have on ISAA another network, say, a DMZ on a ISA DMZ interface and you want to allow the remote site users to access this network too then you need to define a network rule between the DMZ and the remote site, have the proper access rules and make sure that when you create the site-to-site connection on ISAB to specify the IP addresses ranges of this DMZ network into the remote site IP address ranges too.
3. Configure ISAA - The connection to ISAC
Now we will repeat the above steps for creating the site-to-site connection to ISAC.
We’ll name it Branch2:
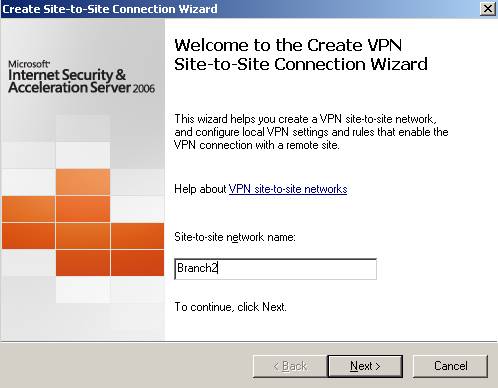
Figure18: The site-to-site connection from ISAA to ISAC
Choose again L2TP/IPsec and enter the server address:
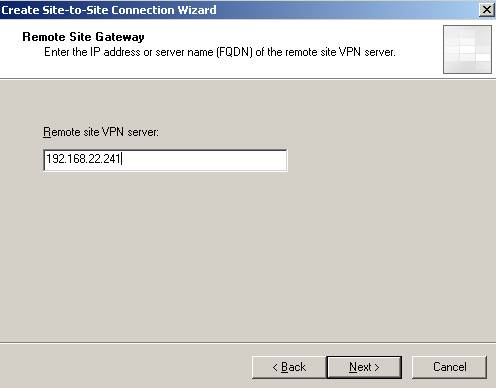
Figure19: The Remote site VPN server
For avoiding confusion let’s call the user Main1.
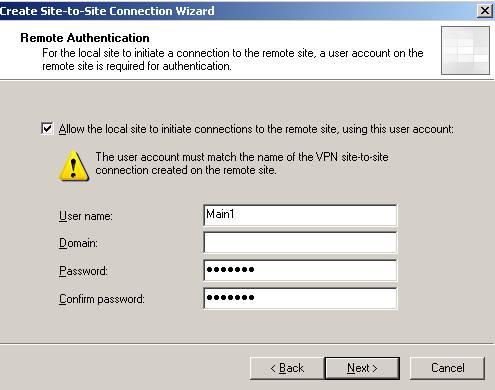
Figure20: User name when ISAA is acting as the Calling Gateway for ISAC
Configure the outgoing authentication method for IKE(I have used the pre-shared key12345qwert). Define the remote site range: 192.168.50.0/24, the access rules and network rule(route relationship).

Figure21: Branch2 remote site on ISAA
Don’t forget about the RRAS setting and uncheck the “Register this connection’s addresses in DNS” for “Branch2” interface.
4. Add the Users Branch and Branch2 on ISAA
And we need to define two users Branch(matching ISAB remote site name from ISAA) and Branch2(matching ISAC remote site name from ISAA) in order to enable ISAA to act as the Answering Gateway for the two site-to-site connections. As said before they will be used byISAB and ISAC. Since ISAA is a domain member we are going to define the users in Active Directory.

Figure22: The users
Don’t forget to set their “Dial-in” permission(you can use “Control access through Remote Access Policy” but let’s keep it simple right now):
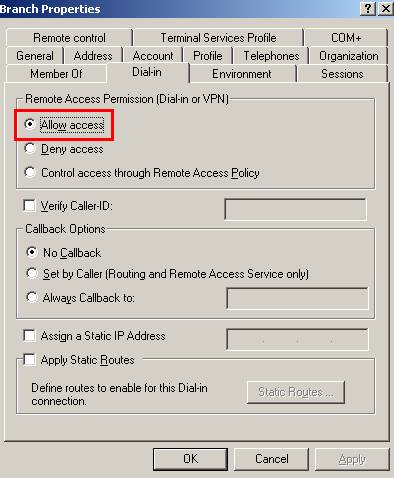
Figure23: Branch user “Dial-in” permission
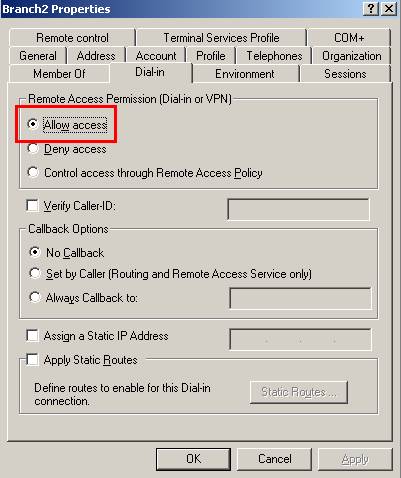
Figure24: Branch2 user “Dial-in” permission
And we are done with ISAA.
Let’s move to ISAB now.
5. Configure ISAB - The connection to ISAA
First we define the site-to-site connection with ISAA.
We'll name it Main(the user name we defined on ISAA in the wizard):
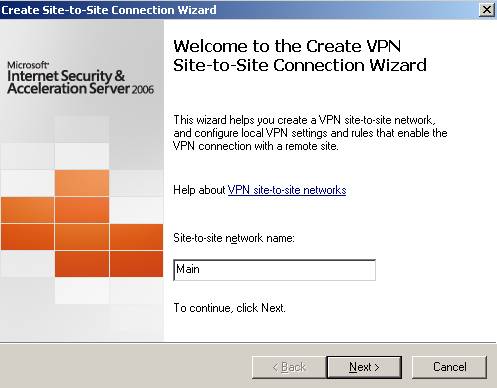
Figure25: Main remote site on ISAB
Choose L2TP/IPsec. Enter ISAA address:
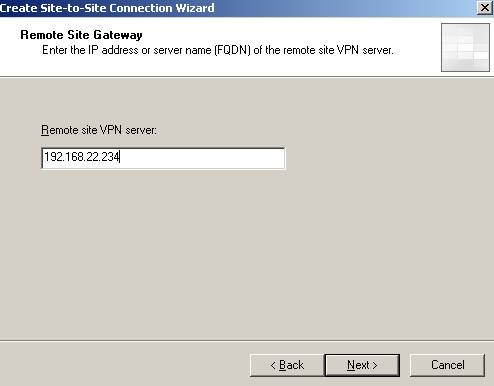
Figure26: The Remote site VPN server
The user name will be Branch since this is how on ISAA is named the remote site.
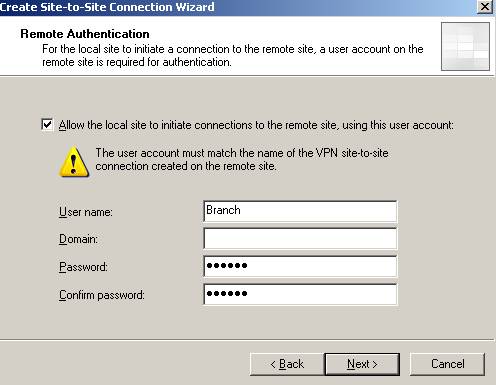
Figure27: The user on ISAB required for ISAB to act as the Calling Gateway
Next, if ISAA is configured to accept incoming connections using pre-shared keys for IKE authentication make sure you fill the correct pre-shared key on ISAB(outgoing authentication):
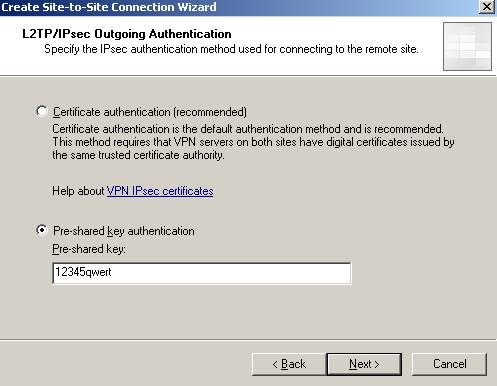
Figure28: Outgoing Authentication on ISAB
And probably you will be prompted for authentication for incoming connections(use the pre-shared key with which ISAA is configured to initialize connections):
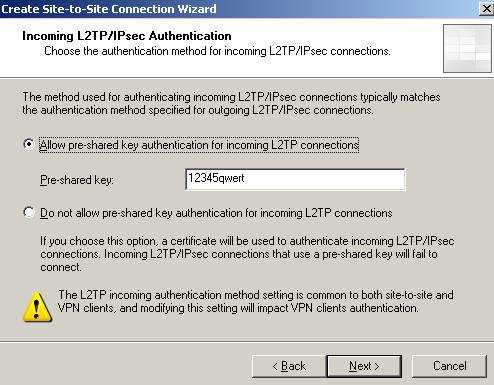
Figure29: Incoming Authentication
OK. I will use everywhere the same pre-shared key. Remember if ISAA acts as the Answering Gateway and ISAB and ISAC as the Calling Gateways, ISAB and ISAC will use the same pre-shared key for outgoing authentication.
The IP address range is 192.168.10.0/24. Create the network rule(route relationship) and access rules.
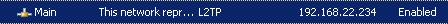
Figure30: Remote site Main on ISAB
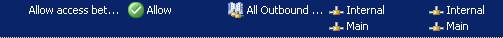
Figure31: Access rules

Figure32: Network rule
Don’t forget about the RRAS setting and uncheck the “Register this connection’s addresses in DNS” for the “Main” interface.
6. Configure ISAB - The connection to ISAC
And now we are going to create the site-to-site VPN connection from ISAB to ISAC. Well call it ToBranch2.
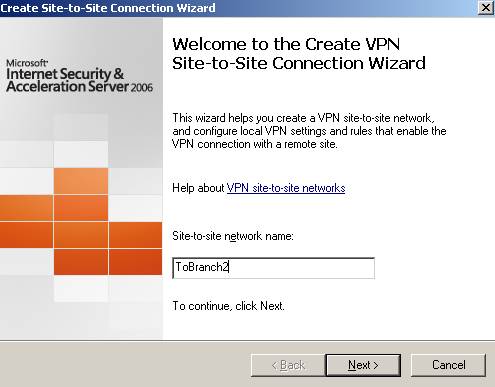
Figure34: The site-to-site VPN connection from ISAB to ISAC
Choose L2TP/IPsec. The ISAC address, 192.168.22.241.
The username, say, ToBranch.
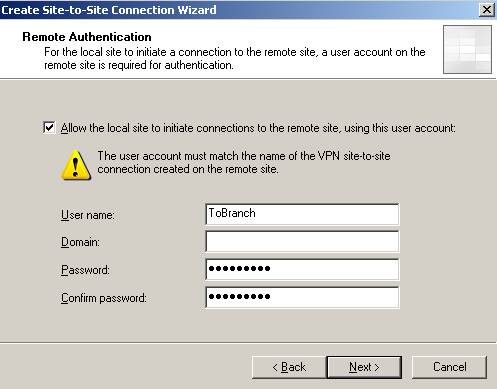
Figure35: The user used by ISAB when acting as the Calling Gateway to ISAC
The outgoing authentication. Both ISAA and ISAB use the same pre-shared key when acting as the Calling Gateway to ISAC.
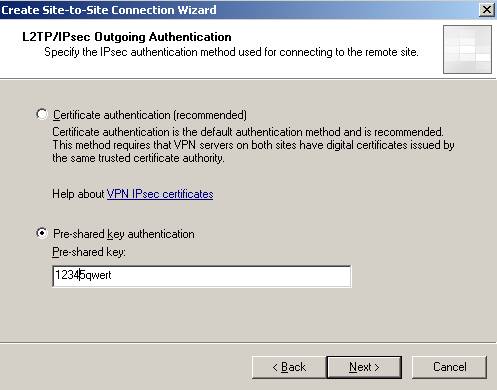
Figure36: The outgoing authentication to ISAC
The IP address range 192.168.50.0/24, then the network rule(route relationship) and the access rules.
Don’t forget about the RRAS setting and uncheck the “Register this connection’s addresses in DNS” for “ToBranch2” interface.
7. Add the Users Main and ToBranch2 on ISAB
Since ISAB is not yet joined to the domain(it will be after the site-to-site connection is up) we will define two local users called Main and, say, ToBranch2 with their “Dial-in” permissions set to allowed.
Figure33: ISAB local users
And ISAB is good to go.
8. Configure ISAC - The connection to ISAA
Moving to ISAC now.
The site-to-site connection to ISAA. We’ll name it Main1 as the user define on ISAA in the wizard.
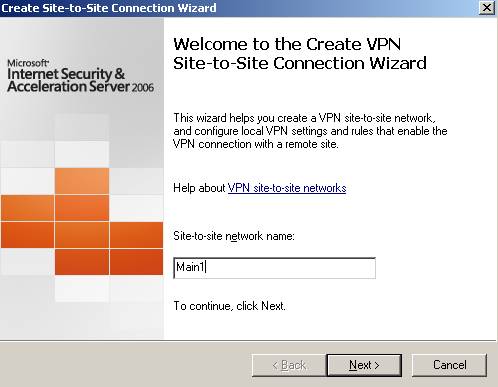
Figure38: The site-to-site VPN connection from ISAC to ISAA
Select the L2TP/IPsec connection. The remote server address is 192.168.22.234.
The user name is Branch2, like the remote site defined on ISAA.
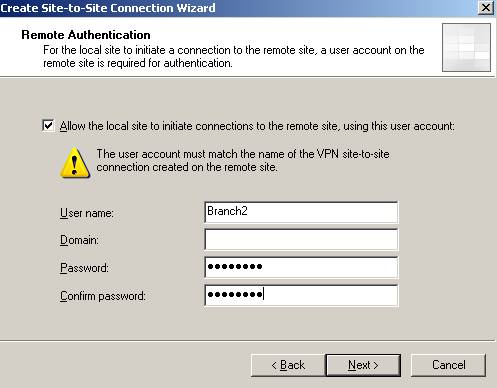
Figure39: The user used by ISAC to act as the Calling Gateway against ISAA
The outgoing authentication.
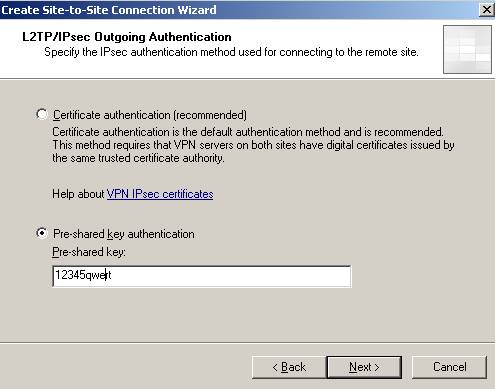
Figure40: The outgoing authentication
If you are prompted for incoming authentication you must match it with one configured on ISAA(for outgoing):
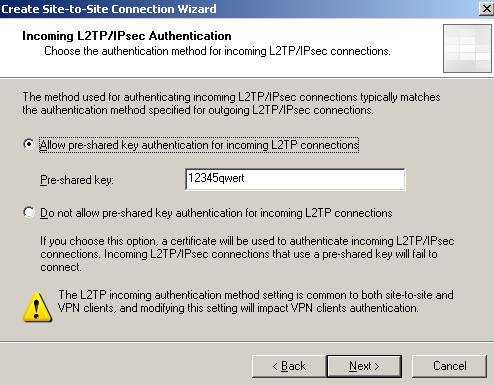
Figure41: The incoming authentication
The IP address range is 192.168.10.0/24. Configure the network rule(route relationship) and the access rules.
Don’t forget about the RRAS setting and uncheck the “Register this connection’s addresses in DNS” for “Main1” interface.
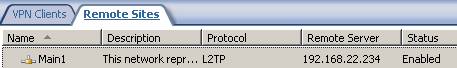
Figure42: Main1 remote site
9. Configure ISAC - The connection to ISAB
Next, the site-to-site VPN from ISAC to ISAB.
We’ll name it ToBranch(like the user define on ISAB in the wizard).
Figure43: ToBranch remote site on ISAC
Choose L2TP/IPsec. The remote server address is 192.168.22.240.
The username is ToBranch2 like the remote site name on ISAB.
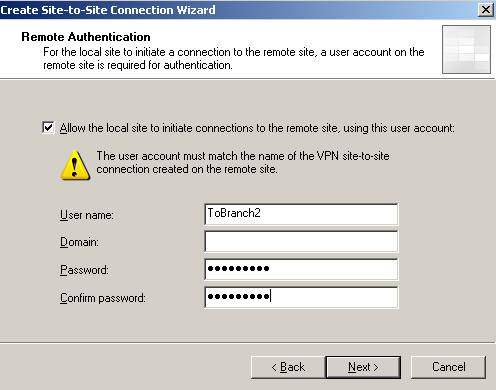
Figure44: The user used by ISAC when acting as the Calling Gateway to ISAB
The outgoing authentication method. Both ISAA and ISAC use the same pre-shared key when acting as the Calling Gateway to ISAB.
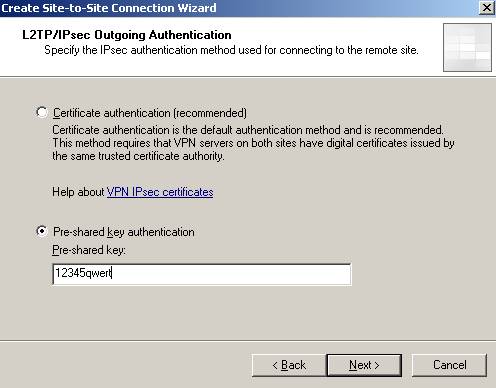
Figure45: The outgoing authentication
The address range is192.168.40.0/24. Configure the network rule(route relationship) and the access rules.

Figure46: ToBranch remote site on ISAC
Don’t forget about the RRAS setting and uncheck the “Register this connection’s addresses in DNS” for “ToBranch” interface.
10. Add the Users Main1 and ToBranch on ISAC
And let’s add two local users(ISAC is not a domain member yet), Main1 and ToBranch with the “Dial-in” permission set to allow.

Figure47: ISAC local users
11. Test the s2s Connections
Let’s try to get the tunnel up from ISAB to ISAA. We are going to use a computer from ISABInternal Network, so ISAB will act as the Calling Gateway and ISAA as the Answering Gateway. So ping from 192.168.40.2 to 192.168.10.2(a computer from ISAA’s Internal Network):
Oops!
My tunnel was already up!
Anyway you should see the replies coming. If not, make sure you have followed the steps correctly.
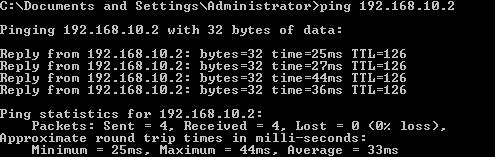
Figure37: LocationA and LocationB connected
Now let’s bring up the tunnel from ISAB to ISAC. Run a ping command from 192.168.40.2 to 192.168.50.10(a host located on ISAC Internal Network)
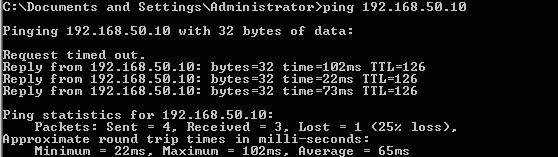
Figure48: LocationB and LocationC connected
And the tunnel from ISAC to ISAA. Another ping from 192.168.50.10 to 192.168.10.2.
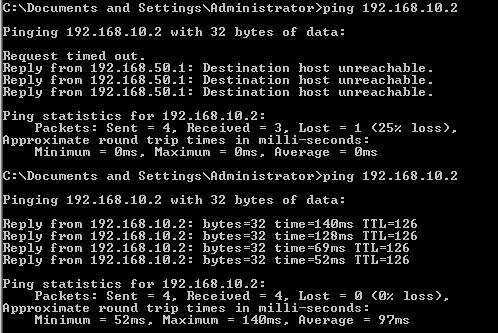
Figure49: LocationC and Location A connected
And now we have connected all three locations through a partial mesh.
And another quick test from 192.168.10.2 to 192.168.40.2 and 192.168.50.10:
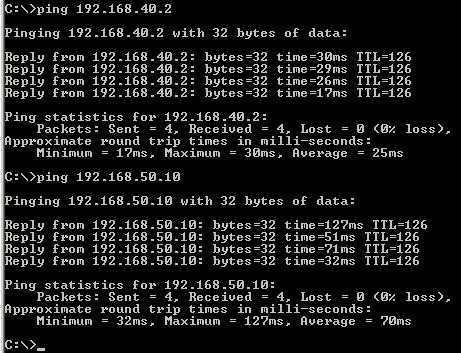
Figure50:LocationA connected to LocationB and LocationC
You can now proceed and join ISAB and ISAC to the domain if you want. Actually if you could, it was better to prepare ISAB and ISAC on LocationA. Install additional domain controllers on LocationB and LocationC and so on.
Remember to use certificates for IKE authentication. Use pre-shared keys only for testing. You can go and configure EAP-TLS for user authentication instead of ms-chapv2.
That’s it!
If you want a related article to ISA Enterprise Edition please refer to the below article:
http://www.microsoft.com/technet/isa/2004/plan/vpn_deployment_ee.mspx
|