|
17.08.2007
Blocking Skype with pfSense and Snort
We have installed pfSense as our network firewall. Make sure you did read its Licence. I will use version 1.0.1.
If you want to find out more about pfSense features please check this page on its site.
Suppose we have two interface on it: Wan and Lan.
And the following rules from Lan to Wan:
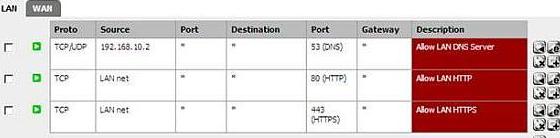
Figure1: pfSense Firewall rules from Lan to Wan
As you can see we have allowed all HTTP/HTTPS traffic.
Skype has the ability to take advantage of this and so it can “get out”.
We want to block it(you might want to block other stuff, but to keep it simple we will talk only about Skype in this article).
Please read these documents first in order to understand how Skype “works”:
An Analysis of the Skype Peer-to-Peer Internet Telephony Protocol.
http://www1.cs.columbia.edu/~salman/skype/
From the last one we can find out how we can block Skype by its signature. For this we will use Snort.
But first let’s install Snort on pfSense. We can find it on the “Packages” menu. See Figure2 and Figure3.
Figure2: Accesing pfSense's Packages
Figure3: pfSense's Packages List
Once installed Snort will appear in the “Installed packages” menu:
Figure4: Installed packages
For configuring Snort we need to access its menu from “Services”:
Figure5: Snort on “Services” Menu
Make sure you put your Oinkmaster code in order to get the updates for rules. As you can see in Figure6, we have an option to block hosts that generate a Snort alert. This sounds great and we will use it for blocking Skype, but you must carefully select what Snort rules are active in order that false alerts to not block legitimate traffic.
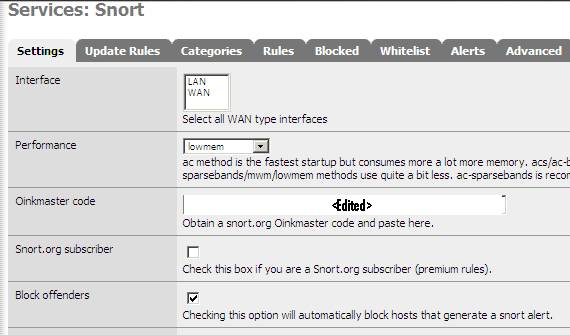
Figure6: Block Offenders
Bellow are the “Categories” of rules we have. For this article I have only selected “p2p.rules”.
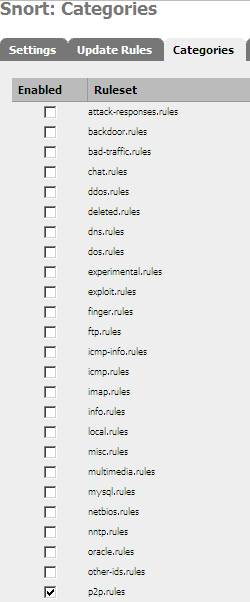
Figure7: Categories: “p2p.rules” checked
Why?
Because as you can see from Figure8 it contains some Skype rules. This rules are enabled.
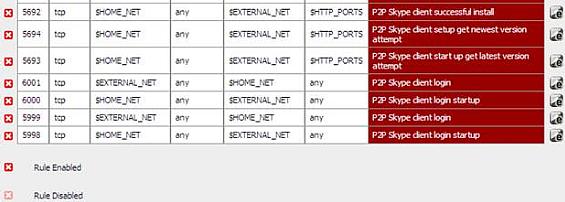
Figure8: Skype rules
What rules actually interests us?
Rules with the SID 5999 and the SID 6001 for example which are enabled.
According to the document, An Analysis of the Skype Peer-to-Peer Internet Telephony Protocol, we are are looking for the “0x17030100” signature which is contained in the login server reply to our client. See Figure9, which is a sample from a Wireshark trace representing a successful Skype login using TCP port 443.
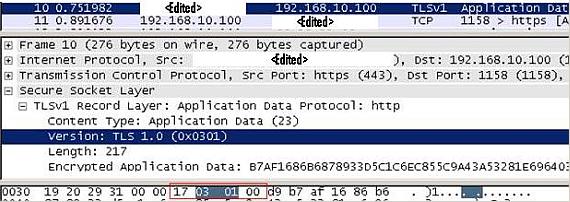
Figure9: Wireshark Trace for “0x17030100” signature”
So we need a Snort rule for traffic coming from “$External_Net” to “Home_Net” which will watch for traffic containing the "0x17030100” signature.
Actually we don’t need to create anything. The rule already exists. There are two: the rules with SID 5999 and SID 6001. See Figure10 and Figure11.
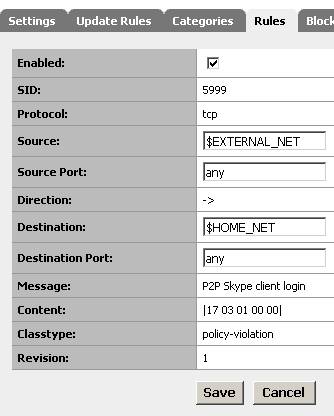
Figure10: Skype rule SID 5999
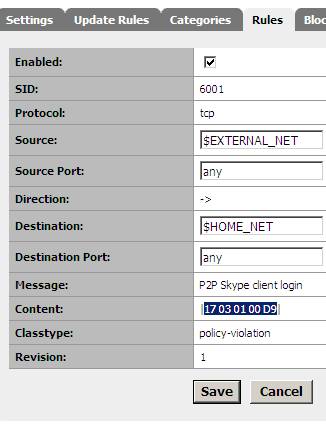
Figure11: Skype rule SID 6001
You can give a search on Snort site and list the available Snort rules. See Figure12.
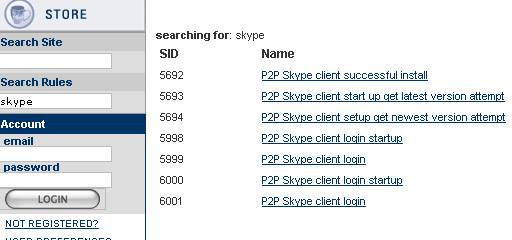
Figure12: Skype Rules listed
The blocked host will appear into the “Blocked” tab and the alert generated by Snort in the “Alerts” tab. Figure13 and Figure14.
Figure13: Blocked Tab
Figure14: Alerts Tab
Since by now we have installed Snort, have the rules in place(selected the “p2p” category and make sure the rules with SID 5999 and SID 5999 are enabled) and we have choosed to block the hosts that generate Snort alerts let’s try to connect with Skype.
Prior of installation of Snort, Skype was able to “get out”:
Figure15: Skype “Connected”
After we installed Snort and configure Pfsense to block host which generate an alert, Skype cannot connect anymore:

Figure16: Skype cannot connect anymore
If we look into the “Alerts” tab we will see that two alerts were generated by the rules with SID 5999 and SID 6001:
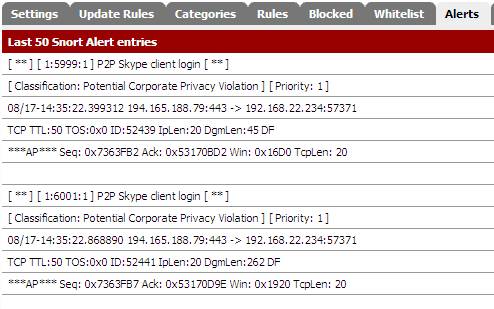
Figure17: Skype Alerts
The “Blocked” tab shows us that a host was blocked. As you can see, it is the login server to which Skype attempted to login.
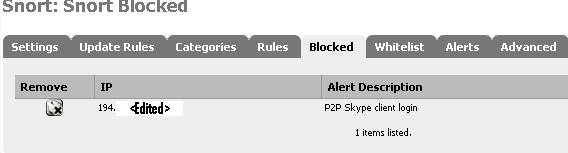
Figure18: Blocked Host So it worked.
It is very simple to block Skype with pfSense and Snort. You must take care what rules you enable because some false alerts might be generated and so legitimate traffic might be blocked.
|