The TLS protocol is based on the SSL 3.0 protocol specifications.
Below are some differences between the two.
1. Key derivation function
TLS makes use of a PRF, a combination of two hash functions(SHA1 and MD5). [1]
SSL 3.0 does not use a PRF, instead makes use abundantly of MD5(half the master secret is generated using only MD5). [2] [4]
2. MAC(Message authentication code)
TLS uses a HMAC construction, as described in [3].
SSL 3.0 uses an older obsolete version of the HMAC construction. [5]
3. Finished messages
TLS 1.0 includes within the Finished message the verify_data(PRF is used to comput it); the verify_data is always 12 octets long.
SSL 3.0 includes within the Finished message two hashes(a MD5 one and a SHA1 one) for verification.
You can see this in the below pictures.
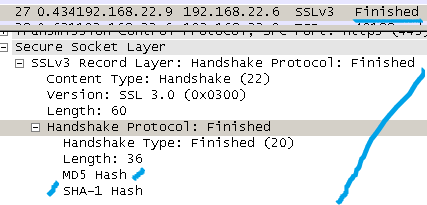
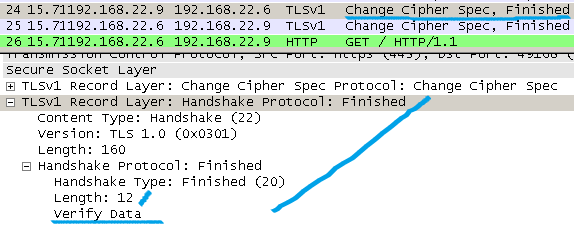
4. RSA key exchange
The SSL 3.0 specifications were not clear about the encoding of public key encrypted data(pre-master secret) [8].
Many SSL 3 implementations just put bytes(encrypted data) directly into the Client Key Exchange message, omitting the length bytes. [4]
You can see this in the below pictures, note the extra length bytes(0x0080) marked with red from the TLS session.
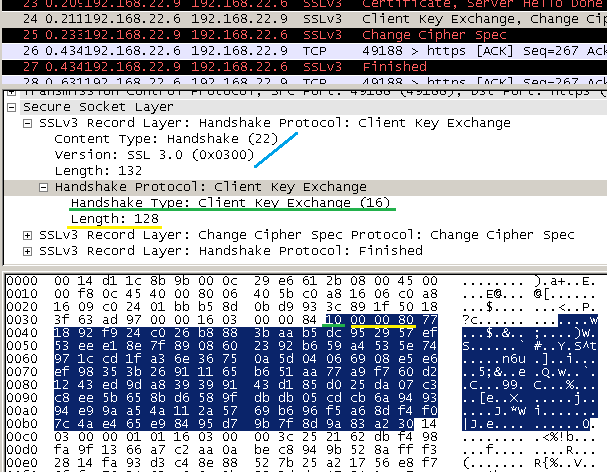
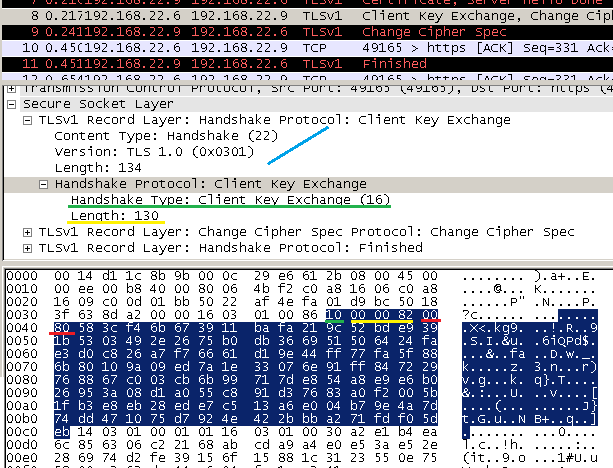
5. Fortezza cipher suites
The Fortezza cipher suites(present in the SSL 3.0 draft) were not included in the TLS 1.0 RFC(because they were not open for public review(IETF policy) [11]).
6. Allow a party to send application data as soon as that party’s Finished message is sent
SSL 3.0 may allow a party to start sending application data as soon as that party’s Finished message is sent. TLS requires a “wait” until the other Finished message is received.
See the Implementation note from Section 5.6.1.2 of [9].
Note that under TLS 1.0 this may be possible for adopters of False Start. [10]
7. Alerts
TLS 1.0 has more alerts compared to SSL 3.0.
- TLS 1.0 alerts(considering only the TLS 1.0 RFC):
close_notify(0)
unexpected_message(10)
bad_record_mac(20)
decryption_failed(21)
record_overflow(22)
decompression_failure(30)
handshake_failure(40)
bad_certificate(42)
unsupported_certificate(43)
certificate_revoked(44)
certificate_expired(45)
certificate_unknown(46)
illegal_parameter(47)
unknown_ca(48)
access_denied(49)
decode_error(50)
decrypt_error(51)
export_restriction(60)
protocol_version(70)
insufficient_security(71)
internal_error(80)
user_canceled(90)
no_renegotiation(100)
- SSL 3.0 alerts(considering only the SSL 3.0 draft):
close_notify(0)
unexpected_message(10)
bad_record_mac(20)
decompression_failure(30)
handshake_failure(40)
no_certificate(41)
bad_certificate(42)
unsupported_certificate(43)
certificate_revoked(44)
certificate_expired(45)
certificate_unknown(46)
8. Mandatory cipher suite
TLS 1.0 specifies TLS_DHE_DSS_WITH_3DES_EDE_CBC_SHA as the mandatory cipher suite.
No such requirement within SSL 3.0.
9. CBC block cipher padding
TLS 1.0 offers a more precise explanation of padding for CBC block cipher, with an example.
See Section 6.2.3.2 of [7].
10.Root CA certificate
In TLS 1.0 , see section 7.4.3 of [7], the root CA certificate may be optionally omitted from the chain within the certificate_list, because certificate validation requires the root keys to be distributed independently.
11. FIPS approved
Although this is not a difference between the protocols themselves, it may worth a note.
TLS 1.0, when properly configured, is approved for FIPS used.
SSL 3.0 it is not approved for use in the protection of Federal information because it relies for certain operations on the use of cryptographic algorithms that are not FIPS approved.
References
[1] TLS 1.0 RFC Section 5 HMAC and the pseudorandom function
http://tools.ietf.org/html/rfc2104
[2] Prohibiting SSL Version 3.0 and Earlier
http://tools.ietf.org/html/draft-turner-ssl-must-not-01
[3] HMAC: Keyed-Hashing for Message Authentication
http://tools.ietf.org/html/rfc2104
[4] NIST SP800-52
http://csrc.nist.gov/publications/nistpubs/800-52/SP800-52.pdf
[5] Analysis of the SSL 3.0 protocol
http://www.schneier.com/paper-ssl-revised.pdf
[6] The SSL Protocol Version 3.0
http://www.mozilla.org/projects/security/pki/nss/ssl/draft302.txt
[7] TLS 1.0 RFC
http://tools.ietf.org/html/rfc2246
[8] TLS 1.2 RFC Section 7.4.7.1
http://tools.ietf.org/html/rfc5246#section-7.4.7.1
[9] SSL 3.0 Draft
http://www.mozilla.org/projects/security/pki/nss/ssl/draft302.txt
[10] Random SSL/TLS 101 - False Start
http://www.carbonwind.net/blog/post/Random-SSLTLS-101-False-Start.aspx
[11] What is TLS/SSL?
http://technet.microsoft.com/en-us/library/cc784450(WS.10).aspx